1、设备恢复出厂设置
1.1、删除配置脚本
delete 605272A.py
1.2、删除默认脚本
delete ipsec_backup.py
delete ipsec_main.py
1.3、恢复出厂设备
set factory-configuration from default
y
1.4、将设备内配置恢复出厂设备
factory-configuration reset
y
1.5、重启设备
reboot
n
y
2、进入设备配置账户密码:
默认账户:admin
默认密码:admin@huawei.com
Login authentication
Username:admin
Password:
Warning: The default password poses security risks.
The password needs to be changed. Change now? [Y/N]: y
ps:如果这里出现密码重复使用,不能设置默认密码,先设置一个临时密码,进入设备,然后使用以下步骤命令修改。
u t m
sys
aaa
local-aaa-user password policy administrator
#进入修改本地AAA用户密码策略
password history record number 0
#密码历史记录是一项安全措施,用于限制用户在一段时间内不能重复使用先前使用过的密码。当密码历史记录数为0时,系统不会保留先前使用的密码信息,即用户可以随意选择以前使用过的密码。
quit
local-user admin password irreversible-cipher Admin@123
3、配置设备联网,从FTP获取升级包;补丁包;脚本文件(忽略)。
3.1、配置联网。
int g0/0/8
ip address x.x.x.x 29
quit
ip route-static 0.0.0.0 0.0.0.0 z.z.z.z
dns server 223.5.5.5
dns resolve
quit
4、应用python脚本。
4.1、安装脚本步骤一。
ops install file
#ops install file ipsecmain.py
#ops install file 606016B_FC_Main.py
4.2、安装脚本步骤二。
sys
ops
script-assistant python
#script-assistant python ipsecmain.py
#script-assistant python 606016B_FC_Main.py
5、将以下配置写进设备保存到开机启动。
5.1、先删除联网路由。
quit
undo ip route-static 0.0.0.0 0.0.0.0
5.2、配置必要命令。
ip vpn-instance underlay_ipsec
ipv4-family
quit
5.3、配置必要命令。
interface GigabitEthernet0/0/8
undo portswitch
description to-wan
undo ipv6 enable
ip binding vpn-instance underlay_ipsec
ip address x.x.x.x 29
tcp adjust-mss 1200
interface GigabitEthernet0/0/7
undo portswitch
description to-ipsec-zihuan
interface GigabitEthernet0/0/7.100 #双机热备这里不用写
interface GigabitEthernet0/0/7.200 #双机热备这里不用写
interface Tunnel0/0/1000
interface Tunnel0/0/1001
quit
ip route-static vpn-instance underlay_ipsec 0.0.0.0 0.0.0.0 z.z.z.z
aaa
local-user admin service-type terminal ssh http
quit
stelnet server enable
ssh server permit interface all
user-interface vty 0
protocol inbound ssh
user-interface vty 1 4
authentication-mode aaa
quit
ip route-static vpn-instance underlay_ipsec 119.145.21.126 255.255.255.255 z.z.z.z tag 4400 description agile-controller
agile controller host 119.145.21.126 port 10020 vpn-instance underlay_ipsec
quit
5.4、将配置写入开机启动,重启设备,验证IPSec和Tunnel是否可以起来。
set factory-configuration from current-configuration
y
factory-configuration reset
y
reboot
n
y
6、故障定位:
故障一
原因:发现Tunnel起不来,系统一直弹日志
报错:日志:
May 18 2023 04:41:47+00:00 Huawei IPSEC/4/IKESAPHASE1ESTABLISHED:OID 1.3.6.1.4.1.2011.6.122.26.6.13 IKE phase1 sa established. (PeerAddress=58.48.71.210, PeerPort=4500, LocalAddress=119.97.235.77, AuthMethod=pre-shared-key, AuthID=58.48.71.210, IDType=IP, VsysName=, Role=Initiator)
<Huawei>
May 18 2023 04:41:51+00:00 Huawei IPSEC/4/IPSECNEGOFAIL:OID 1.3.6.1.4.1.2011.6.122.26.6.14 IPSec tunnel negotiation fails. (Ifindex=11, SeqNum=0, Reason=flow or peer mismatch, ReasonCode=4, PeerAddress=58.48.71.210, PeerPort=4500, VsysName=, InterfaceName=GigabitEthernet0/0/8, ConnID=0)
Huawei>
May 18 2023 04:41:58+00:00 Huawei IPSEC/4/IPSECNEGOFAIL:OID 1.3.6.1.4.1.2011.6.122.26.6.14 IPSec tunnel negotiation fails. (Ifindex=11, SeqNum=0, Reason=flow or peer mismatch, ReasonCode=4, PeerAddress=58.48.71.210, PeerPort=4500, VsysName=, InterfaceName=GigabitEthernet0/0/8, ConnID=0)
<Huawei>
May 18 2023 04:42:07+00:00 Huawei IPSEC/4/IPSECNEGOFAIL:OID 1.3.6.1.4.1.2011.6.122.26.6.14 IPSec tunnel negotiation fails. (Ifindex=11, SeqNum=0, Reason=flow or peer mismatch, ReasonCode=4, PeerAddress=58.48.71.210, PeerPort=4500, VsysName=, InterfaceName=GigabitEthernet0/0/8, ConnID=0)
<Huawei>
May 18 2023 04:42:13+00:00 Huawei %%01NQA/4/RISING_ALARM(l)[19]:The 2 defined in nqa alarm table(OwnerIndex=admin TestName=ipsecmain AlarmEntryNumber=1)has alarm value 100,going out of threshold 100.It's alarm sample type is 2.
<Huawei>
May 18 2023 04:42:13+00:00 Huawei IPSEC/4/IPSECRESETIKESA:OID 1.3.6.1.4.1.2011.6.122.26.6.7 Reset IKE SA. (VsysName=)
Huawei>
May 18 2023 04:42:13+00:00 Huawei IPSEC/4/IPSECRESETIPSECSA:OID 1.3.6.1.4.1.2011.6.122.26.6.8 Reset IPSec SA. (VsysName=)
<Huawei>
May 18 2023 04:42:13+00:00 Huawei %%01OPSA/2/SCRIPT_LOG(l)[20]:OPS: ops:reset ipsec 58.48.71.210 success (user="ipsecmain.py", session=3870067256).
<Huawei>
May 18 2023 04:42:16+00:00 Huawei IPSEC/4/IPSECNEGOFAIL:OID 1.3.6.1.4.1.2011.6.122.26.6.14 IPSec tunnel negotiation fails. (Ifindex=11, SeqNum=0, Reason=flow or peer mismatch, ReasonCode=4, PeerAddress=58.48.71.210, PeerPort=4500, VsysName=, InterfaceName=GigabitEthernet0/0/8, ConnID=0)
日志解读:
1、第一条日志(Huawei IPSEC/4/IKESAPHASE1ESTABLISHED)表示IKE(Internet Key Exchange)阶段1安全联盟已建立。其中提供了对等地址(PeerAddress)、对等端口(PeerPort)、本地地址(LocalAddress)、认证方法(AuthMethod)、认证ID(AuthID)、ID类型(IDType)等详细信息。
2、接下来的几条日志(Huawei IPSEC/4/IPSECNEGOFAIL)表示IPSec隧道协商失败。提供了失败的原因(Reason)、原因代码(ReasonCode)、对等地址(PeerAddress)、对等端口(PeerPort)、接口名称(InterfaceName)等信息。
3、最后几条日志中(Huawei %%01NQA/4/RISING_ALARM、Huawei IPSEC/4/IPSECRESETIKESA、Huawei IPSEC/4/IPSECRESETIPSECSA、Huawei %%01OPSA/2/SCRIPT_LOG)提供了关于NQA(Network Quality Analysis)告警、重置IKE SA和IPSec SA的信息,以及关于重置IPSec的操作日志。
故障二
原因:发现Tunnel起不来,系统还是弹日志,但是跟第一次日志不一样。
报错:日志:
May 18 2023 04:54:55+00:00 Huawei %%01NQA/4/RISING_ALARM(l)[7]:The 2 defined in nqa alarm table(OwnerIndex=admin TestName=ipsecmain AlarmEntryNumber=1)has alarm value 100,going out of threshold 100.It's alarm sample type is 2.
<Huawei>
May 18 2023 04:54:56+00:00 Huawei IPSEC/4/IPSECRESETIKESA:OID 1.3.6.1.4.1.2011.6.122.26.6.7 Reset IKE SA. (VsysName=)
<Huawei>
May 18 2023 04:54:56+00:00 Huawei IPSEC/4/IPSECRESETIPSECSA:OID 1.3.6.1.4.1.2011.6.122.26.6.8 Reset IPSec SA. (VsysName=)
<Huawei>
May 18 2023 04:54:56+00:00 Huawei IPSEC/4/IPSECTUNNELSTOP:OID 1.3.6.1.4.1.2011.6.122.26.6.2 The IPSec tunnel is deleted. (Ifindex=11, SeqNum=10, TunnelIndex=4026531848, RuleNum=1, DstIP=58.48.71.210, InsideIP=10.200.200.30, RemotePort=4500, CpuID=0, SrcIP=119.97.235.77, FlowInfo=Source: 10.50.37.151/255.255.255.255:0-65535 Destination: 10.200.200.30/255.255.255.255:0-65535 Protocol: 0 DSCP: 255, OfflineReason=config modify or manual offline, VsysName=, InterfaceName=GigabitEthernet0/0/8, SlotID=0)
<Huawei>
May 18 2023 04:54:56+00:00 Huawei %%01OPSA/2/SCRIPT_LOG(l)[8]:OPS: ops:reset ipsec 58.48.71.210 success (user="ipsecmain.py", session=3909083944).
<Huawei>
May 18 2023 04:54:59+00:00 Huawei IPSEC/4/IKESAPHASE1ESTABLISHED:OID 1.3.6.1.4.1.2011.6.122.26.6.13 IKE phase1 sa established. (PeerAddress=58.48.71.210, PeerPort=4500, LocalAddress=119.97.235.77, AuthMethod=pre-shared-key, AuthID=58.48.71.210, IDType=IP, VsysName=, Role=Initiator)
<Huawei>
May 18 2023 04:55:00+00:00 Huawei IPSEC/4/IPSECTUNNELSTART:OID 1.3.6.1.4.1.2011.6.122.26.6.1 The IPSec tunnel is established. (Ifindex=11, SeqNum=10, TunnelIndex=4026531849, RuleNum=1, DstIP=58.48.71.210, InsideIP=10.200.200.30, RemotePort=4500, CpuID=0, SrcIP=119.97.235.77, FlowInfo=Source: 10.50.37.151/255.255.255.255:0-65535 Destination: 10.200.200.30/255.255.255.255:0-65535 Protocol: 0 DSCP: 255, LifeSize=1843200, LifeTime=3600, VsysName=, InterfaceName=GigabitEthernet0/0/8, SlotID=0, Role=Initiator)
<Huawei>
May 18 2023 04:55:10+00:00 Huawei %%01CFMY/4/DEVICE_REG_FAILURE(l)[9]:Device failed to register to AC. (Host= 119.145.21.126, Port= 10020, LastFailReason= the device is not added to the controller, VPNName= underlay_ipsec).
日志解读:
1、第一条日志(Huawei %%01NQA/4/RISING_ALARM)表示NQA(Network Quality Analysis)告警触发。其中提供了告警类型(2)、告警值(100)、阈值(100)等详细信息。
2、接下来的几条日志(Huawei IPSEC/4/IPSECRESETIKESA、Huawei IPSEC/4/IPSECRESETIPSECSA)表示重置IKE SA和IPSec SA。
3、"May 18 2023 04:54:56+00:00 Huawei IPSEC/4/IPSECTUNNELSTOP" 表示IPSec隧道已删除。提供了隧道的详细信息,包括接口索引(Ifindex)、隧道索引(TunnelIndex)、对等地址(DstIP)、本地地址(InsideIP)、远程端口(RemotePort)、接口名称(InterfaceName)等。
4、"May 18 2023 04:54:56+00:00 Huawei %%01OPSA/2/SCRIPT_LOG" 表示重置IPSec操作的日志。
5、"May 18 2023 04:54:59+00:00 Huawei IPSEC/4/IKESAPHASE1ESTABLISHED" 表示IKE阶段1安全联盟已建立。
6、"May 18 2023 04:55:00+00:00 Huawei IPSEC/4/IPSECTUNNELSTART" 表示IPSec隧道已建立。
7、"May 18 2023 04:55:10+00:00 Huawei %%01CFMY/4/DEVICE_REG_FAILURE" 表示设备注册失败到AC(Access Controller)。提供了失败的详细原因(LastFailReason)等信息。
问题定位:
解决:发现是脚本问题,重新FTP上传修改正确的脚本,执行以下命令,重新安装脚本。
ops uninstall file python.py
system
ops
undo script-assistant python python.py
quit
quit
ops install file python.py
system
ops
script-assistant python python.py
quit
quit
reboot
n
y
检查IPSec:检查IPSec是否起来。
dis ike sa
<Huawei>dis ike sa
Conn-ID | Peer | VPN | Flag(s) | Phase | RemoteType | RemoteID
2 | 58.48.71.210/4500 | underlay_ipsec | RD|ST|A | v1:2 | IP | 58.48.71.210
1 | 58.48.71.210/4500 | underlay_ipsec | RD|ST|A | v1:1 | IP | 58.48.71.210
Number of IKE SA : 2
Flag Description:
RD--READY ST--STAYALIVE RL--REPLACED FD--FADING TO--TIMEOUT
HRT--HEARTBEAT LKG--LAST KNOWN GOOD SEQ NO. BCK--BACKED
M--ACTIVE S--STANDBY A--ALONE NEG--NEGOTIATING
dis ipsec sa
<Huawei>dis ipsec sa
ipsec sa information:
==========================
Interface: GigabitEthernet0/0/8
IPSec policy name: "S2S-IPSEC"
Sequence number : 10
Acl group : 3333/IPv4
Acl rule : 1
Mode : ISAKMP
Connection ID : 2
Tunnel index : 4026531841
Encapsulation mode: Tunnel
Holding time : 0d 0h 1m 13s
Tunnel local : 119.97.235.77/4500
Tunnel remote : 58.48.71.210/4500
Flow source : 10.50.37.151/255.255.255.255 0/0-65535
Flow destination : 10.200.200.30/255.255.255.255 0/0-65535
Flow vpn : underlay_ipsec
[Outbound ESP SAs]
SPI: 4949125 (0x4b8485)
Proposal: ESP-ENCRYPT-3DES-192 ESP-AUTH-SHA1
SA remaining soft duration (kilobytes/sec): 1290239/2447
SA remaining hard duration (kilobytes/sec): 1843199/3527
Outpacket count : 15
Outpacket encap count : 15
Outpacket drop count : 0
Max sent sequence-number: 15
UDP encapsulation used for NAT traversal: Y
[Inbound ESP SAs]
SPI: 6328603 (0x60911b)
Proposal: ESP-ENCRYPT-3DES-192 ESP-AUTH-SHA1
SA remaining soft duration (kilobytes/sec): 1290239/2447
SA remaining hard duration (kilobytes/sec): 1843199/3527
Inpacket count : 15
Inpacket decap count : 15
Inpacket drop count : 0
Max received sequence-number: 15
UDP encapsulation used for NAT traversal: Y
Anti-replay : Enable
Anti-replay window size: 1024
检查Tunnel:检查Tunnel是否起来。
ping -vpn-instance underlay_ipsec PE-IP
#underlay_ipsec (是你Tunnel的VRF)
7、复制esn到中控的站点设备,进行开局。
display esn
8、中控配置。
8.1、添加站点。
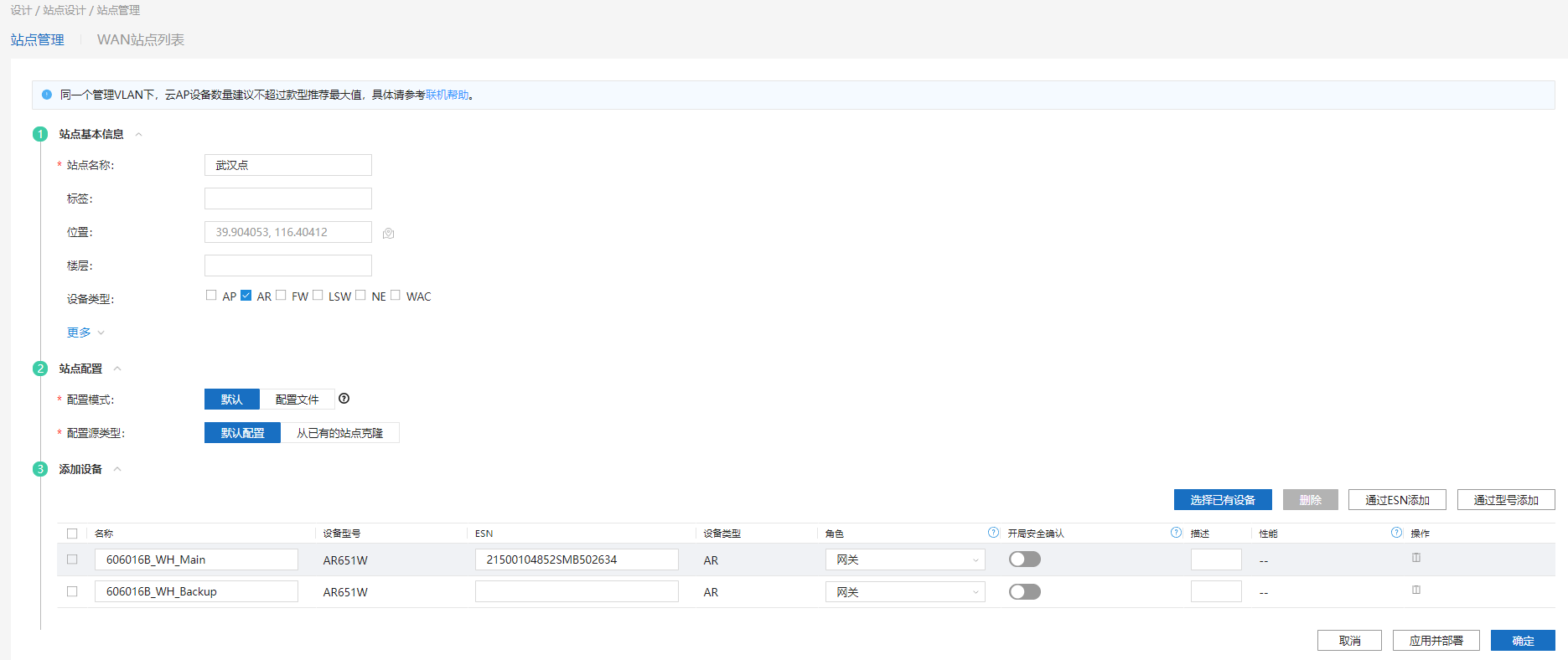
8.2、底层查看是否连上中控,显示Success。
dis ag st
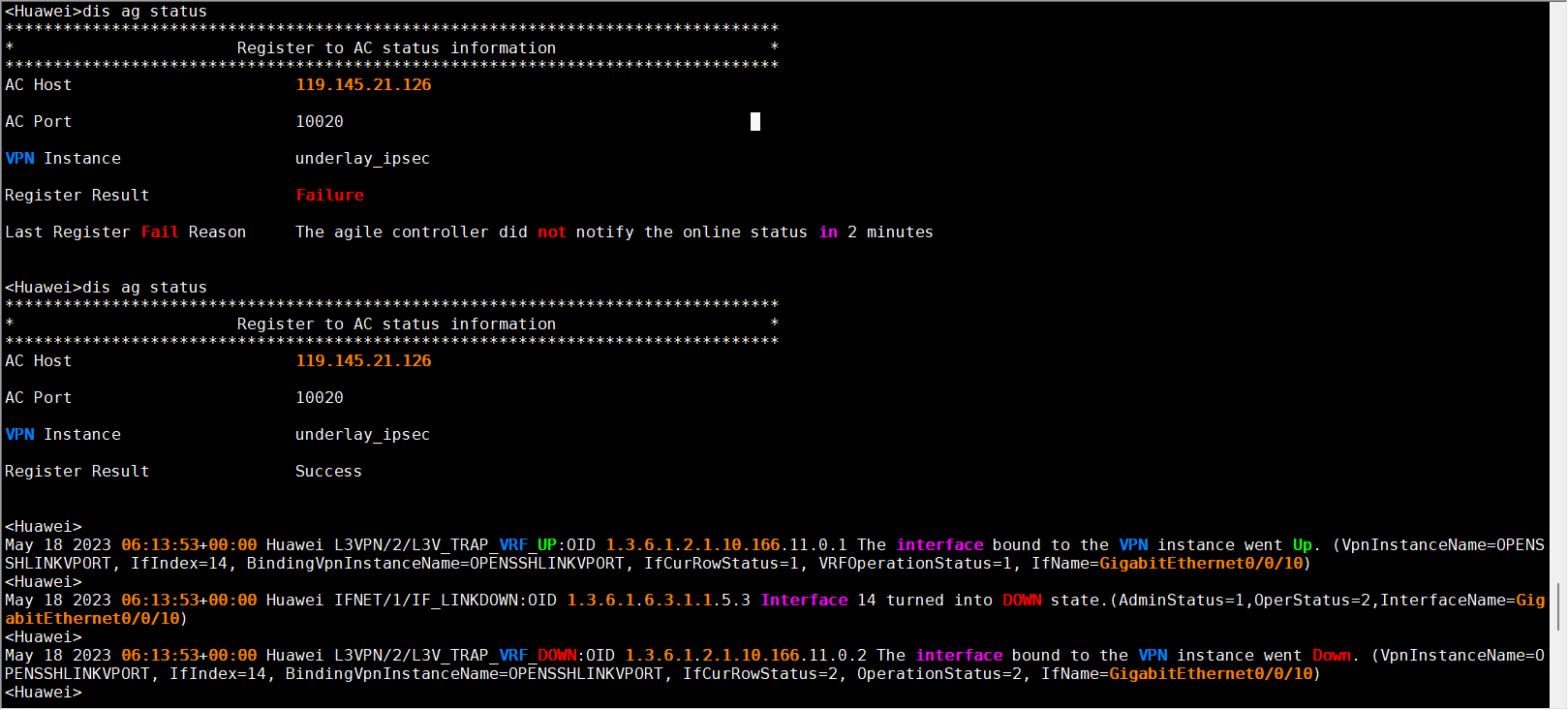
8.3、中控刷新页面查看,设备是否连上中控。

8.4、中控查看配置结果:成功。
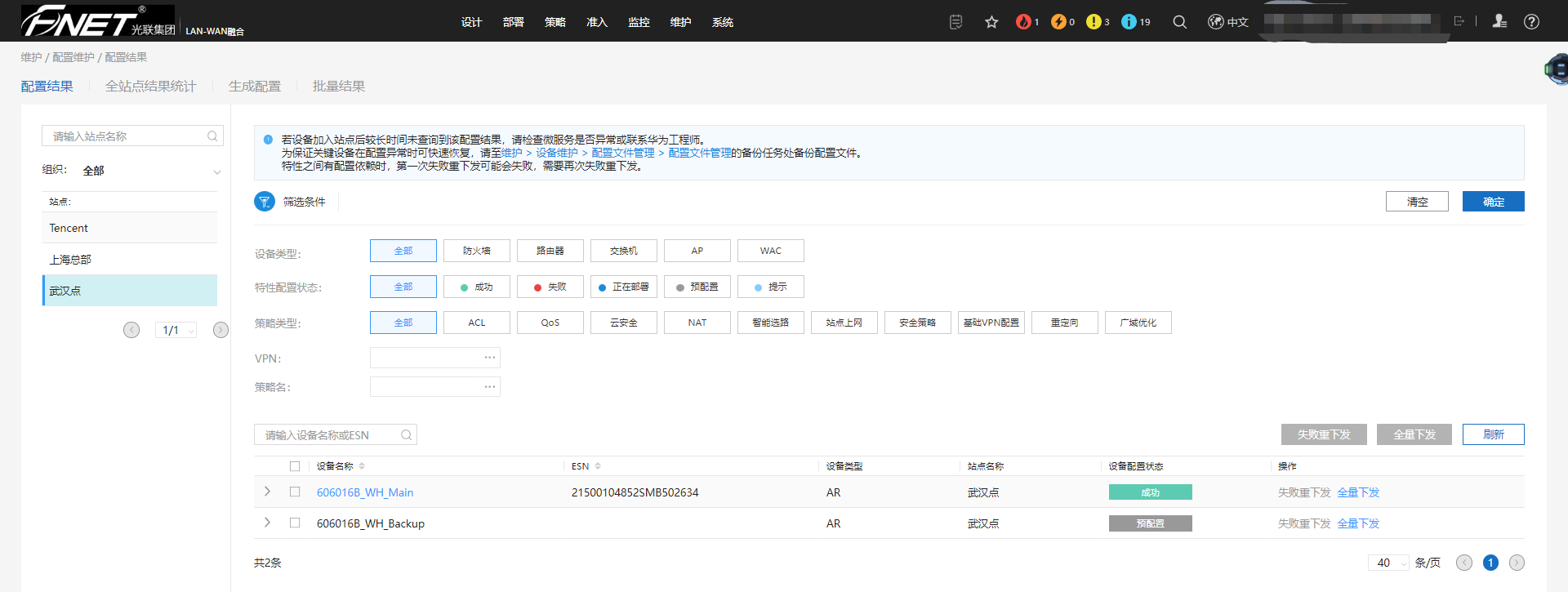
8.5、部署---WAN物理网络配置。
8.5.1、配置ZTP开局。
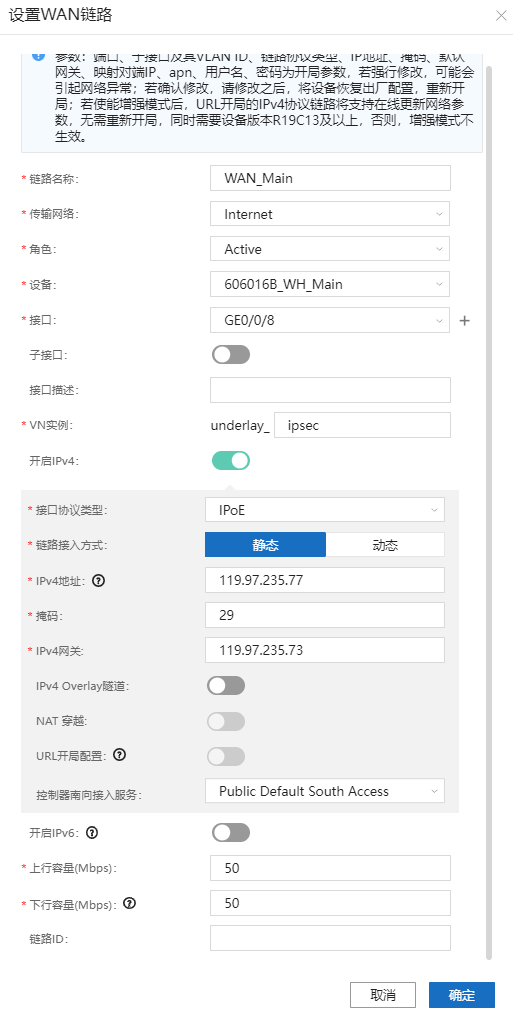
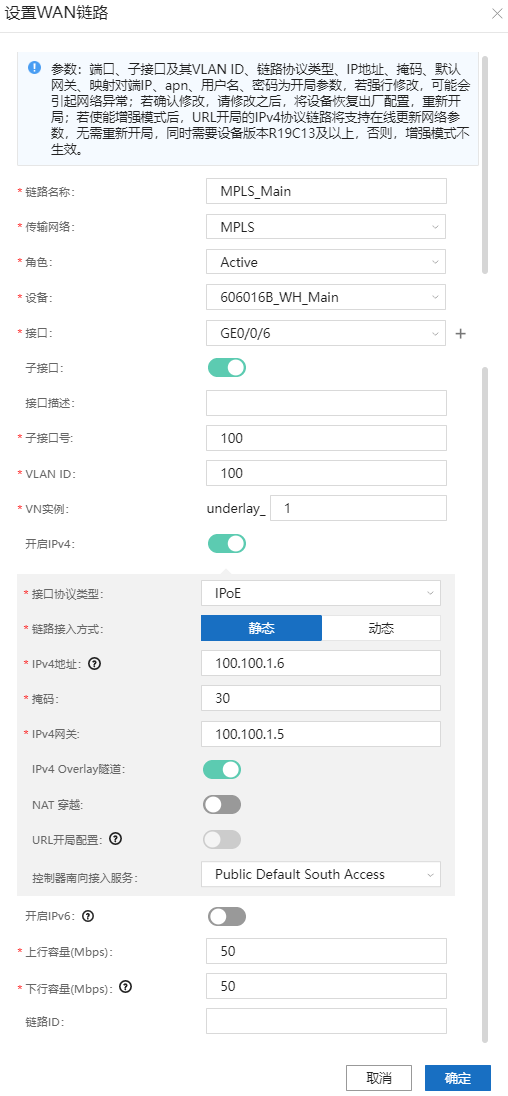
8.5.4、配置心跳口。

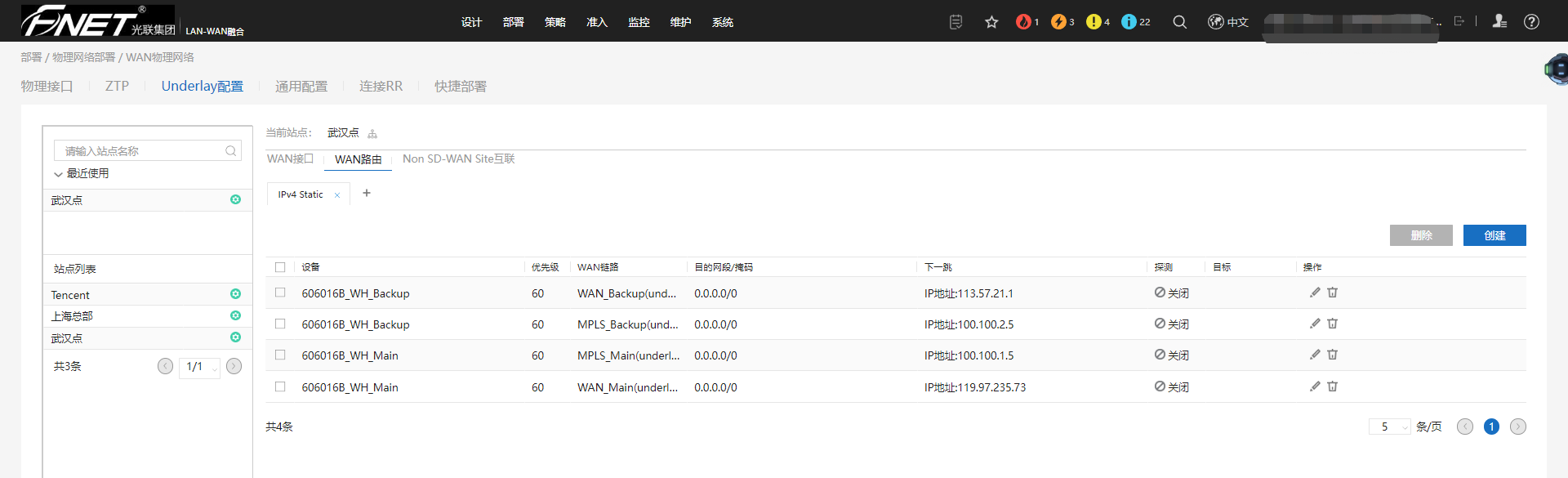
8.5.3、配置Underlay。
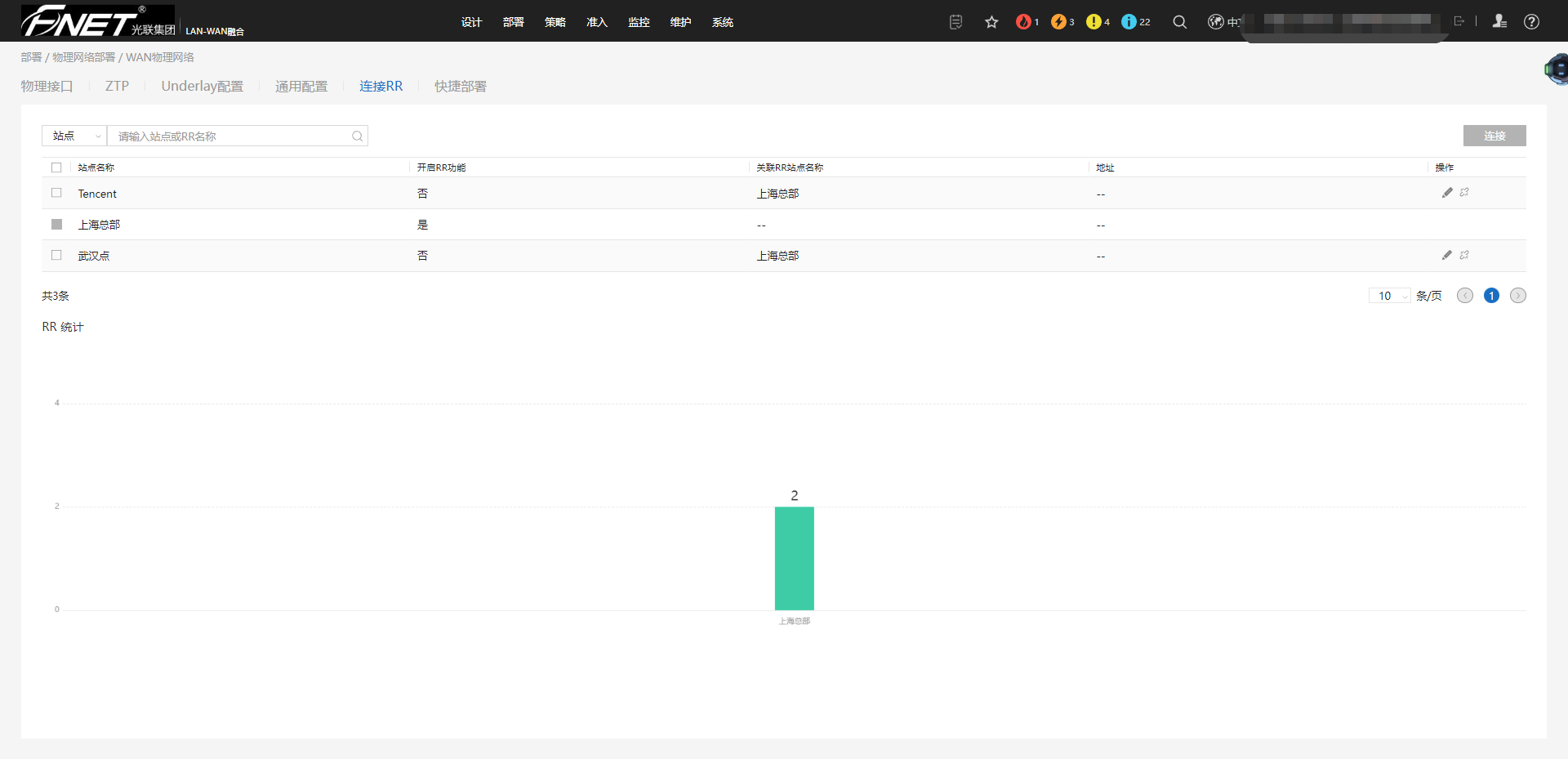
8.5.4、连接RR配置。
8.6、部署---WAN虚拟网络配置。
8.6.1、虚拟网络管理。

8.6.2、拓扑。
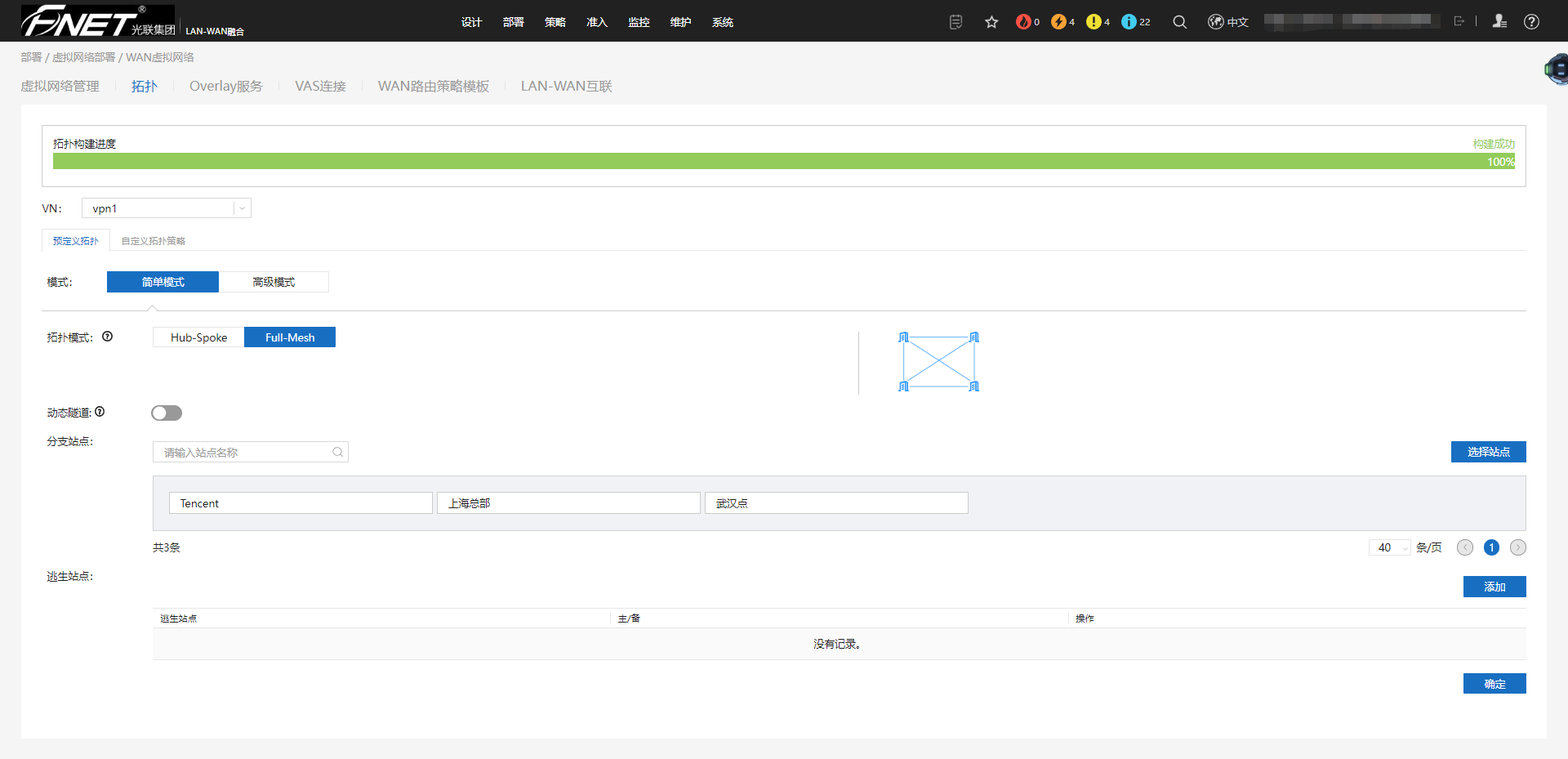
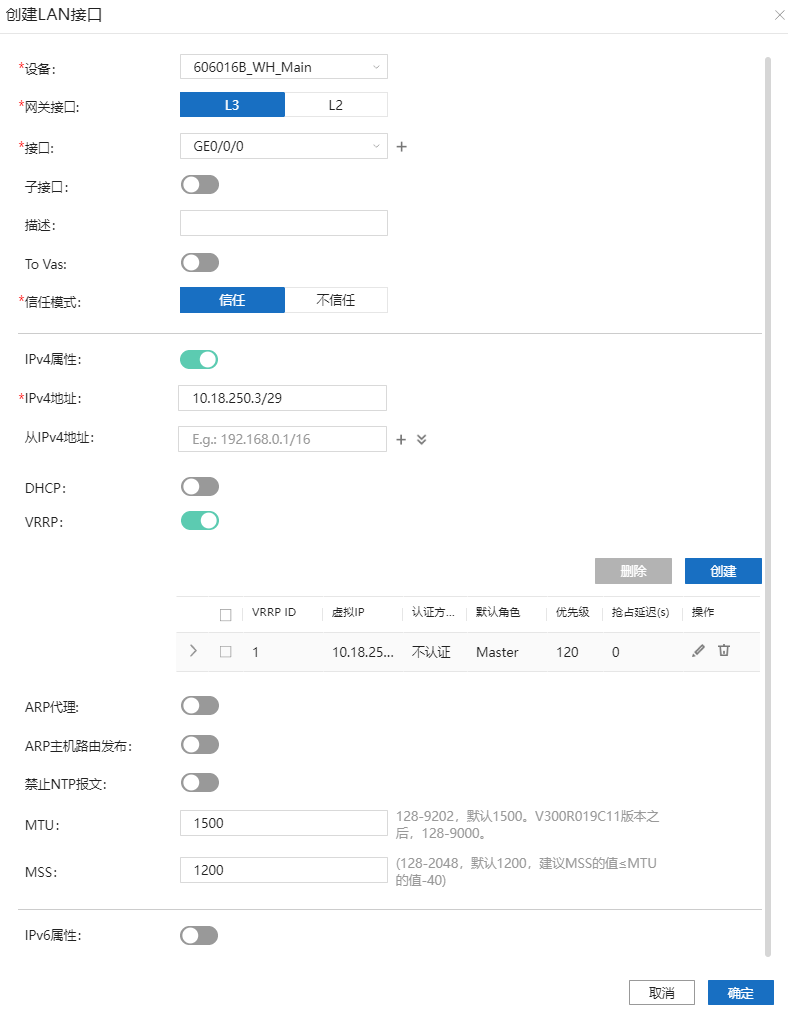
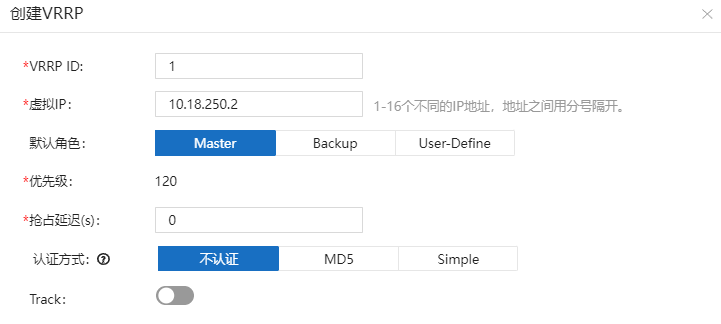
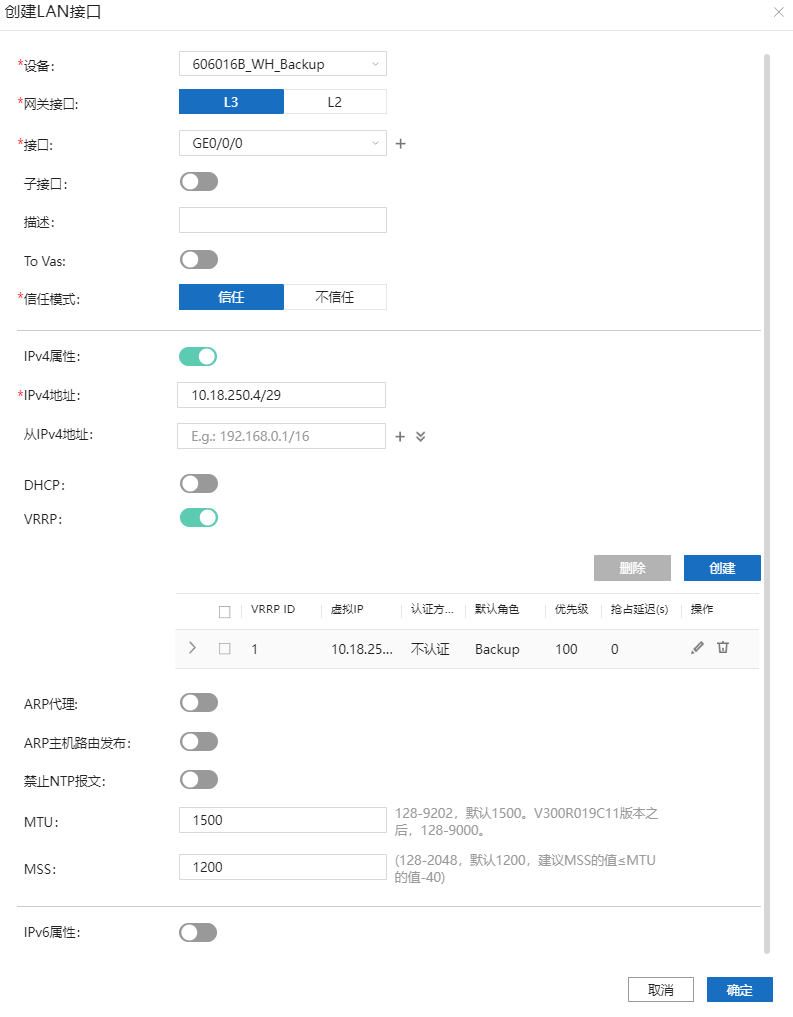
8.6.3、配置Overlay。
主LAN口。
备LAN口。
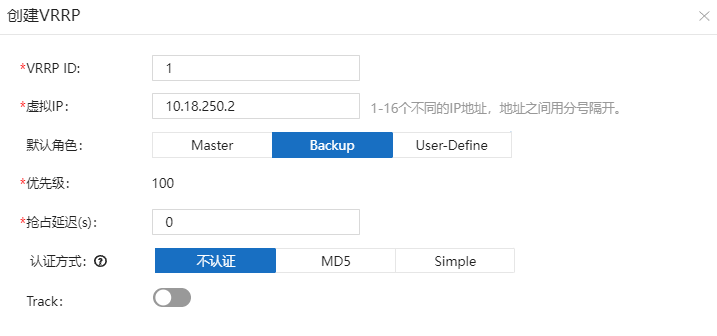
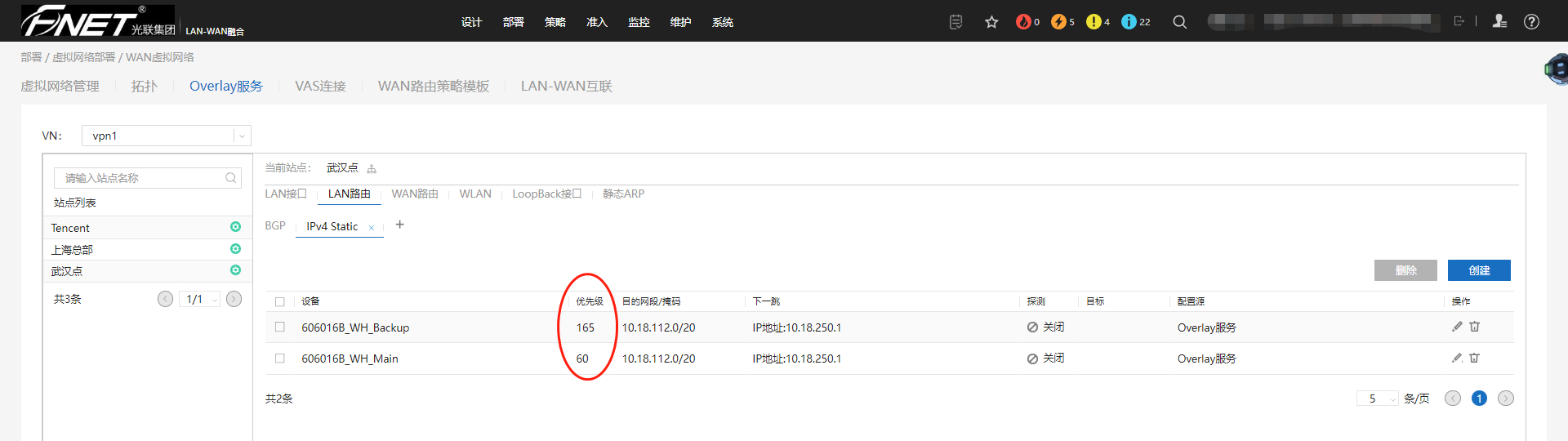
LAN路由。
9、业务状态dtls;evpn检查。
dis dtls peer-connection status
查看对等体状态。

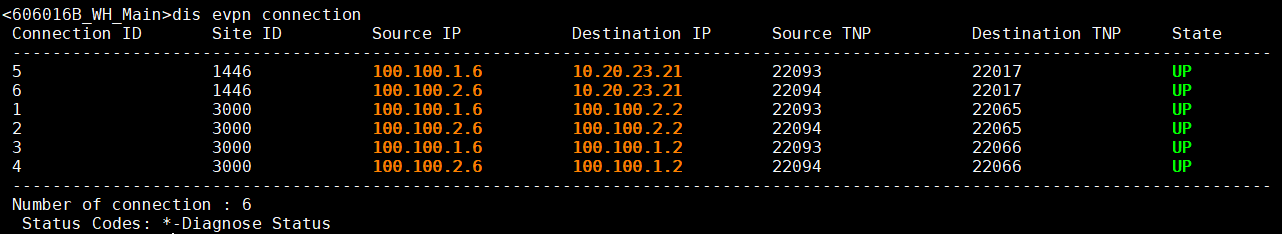
dis evpn connection
查看EVPN连接状态。
10、业务功能验证。
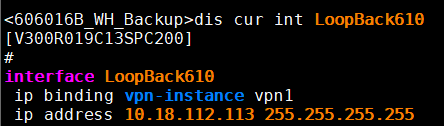
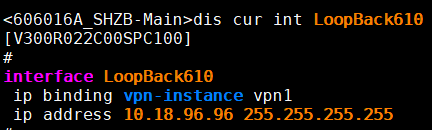
10.1、腾讯云配置LoopBack接口。
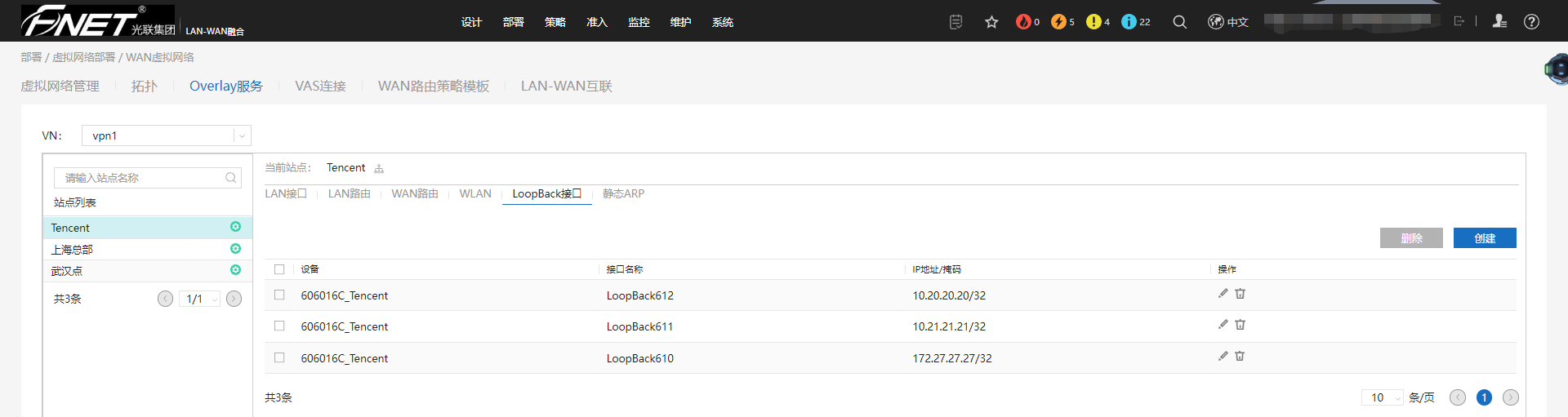
10.2、上海总部配置LoopBack接口。
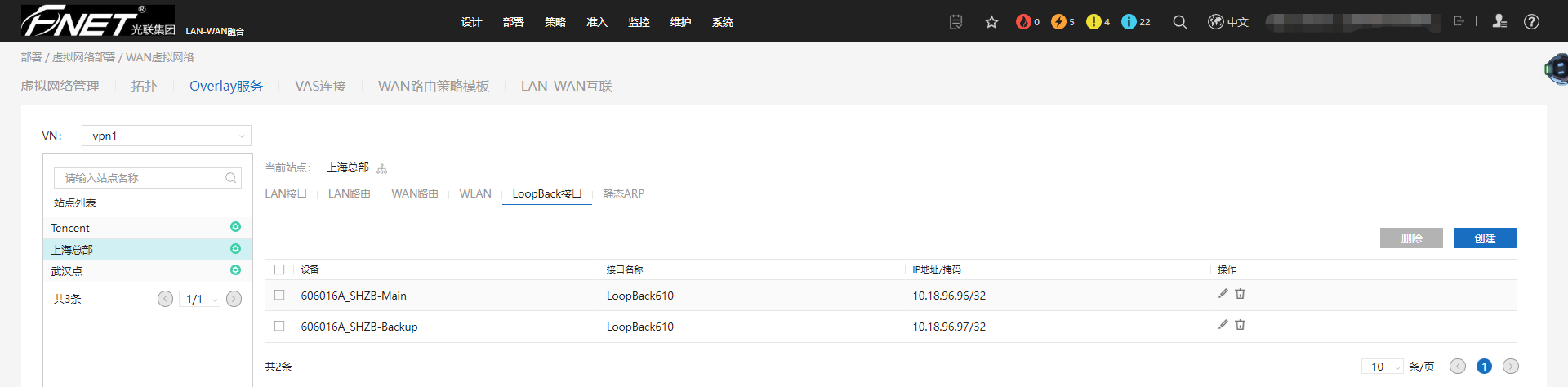
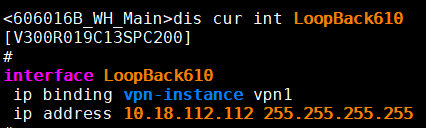
10.3、武汉点配置LoopBack接口。

10.4、ping测试
10.4.1、 腾讯云ping,tracert上海主

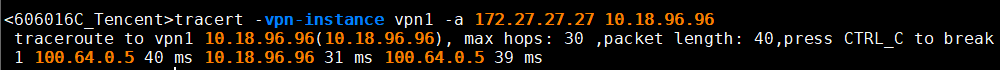
10.4.2、 腾讯云ping,tracert上海备



10.4.3、 腾讯云ping,tracert武汉主
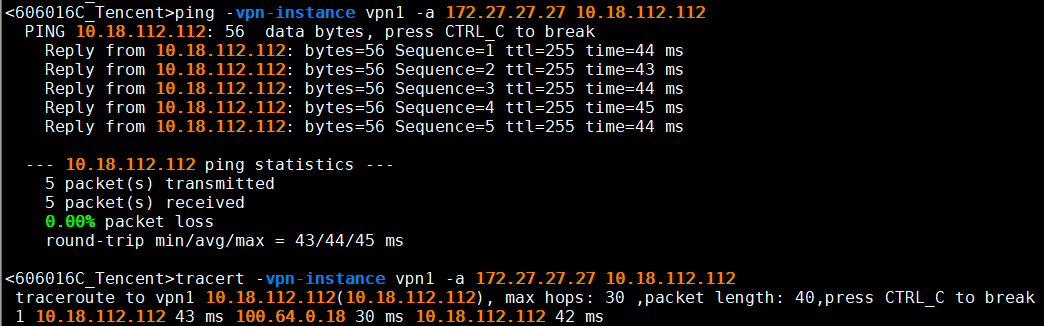
10.4.4、 腾讯云ping,tracert武汉备