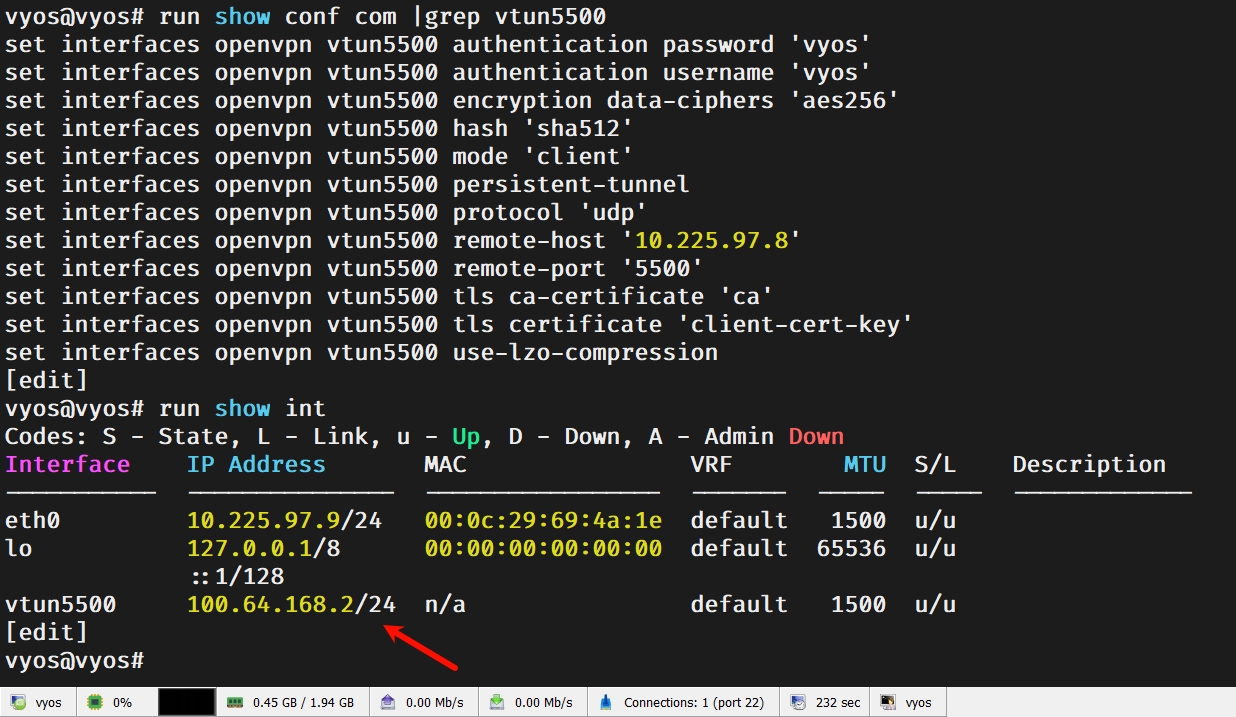
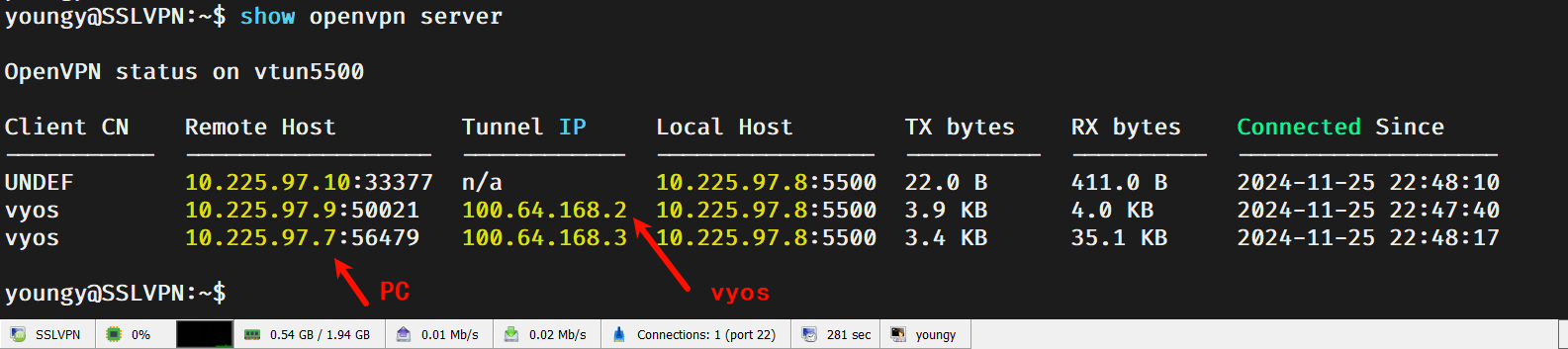
文章介绍:使用官方vyos-1.5 滚动版搭建openvpn服务,支持分支vyos拨号组网,支持移动终端例如win电脑,手机等设备拨号连接内网。
一、参考资料
二、VyOS 镜像下载
三、安装 VyOS
3.1、安装
3.2、基础配置
set interfaces ethernet eth0 address '10.225.97.8/24'
set protocols static route 0.0.0.0/0 next-hop 10.225.97.6
set service ssh port '22'
set system name-server '223.5.5.5'
set system name-server '223.6.6.6'
set nat source rule 100 outbound-interface name 'eth0'
set nat source rule 100 source address '100.64.168.0/24'
set nat source rule 100 translation address 'masquerade'
四、配置OpenVPN
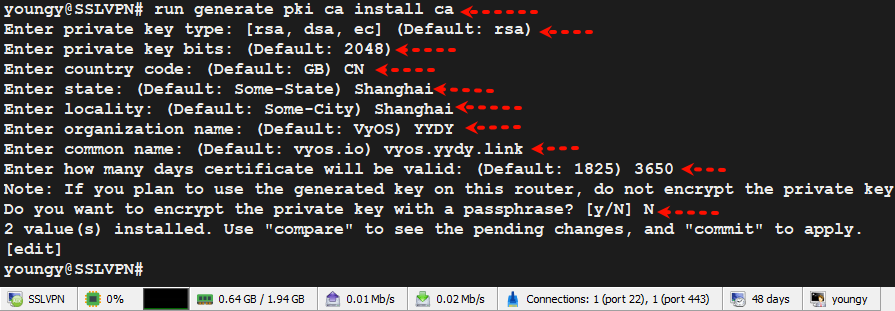
4.1、生成ca证书
run generate pki ca install ca
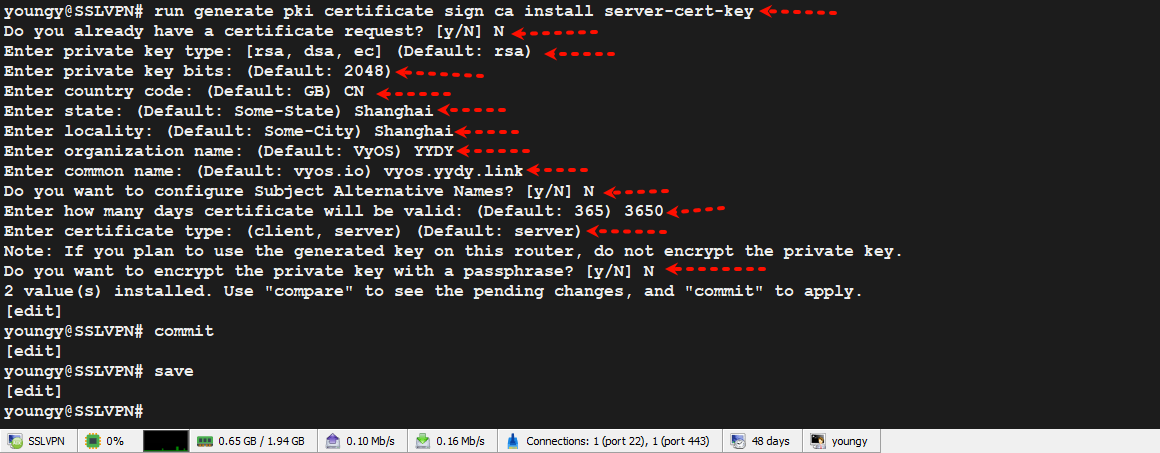
4.2、生成服务端证书和密钥
run generate pki certificate sign ca install server-cert-key
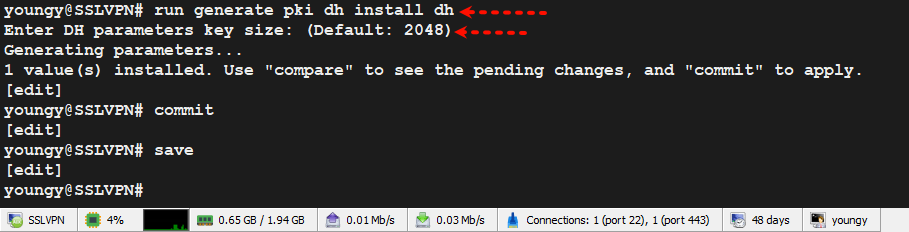
4.3、生成DH
run generate pki dh install dh
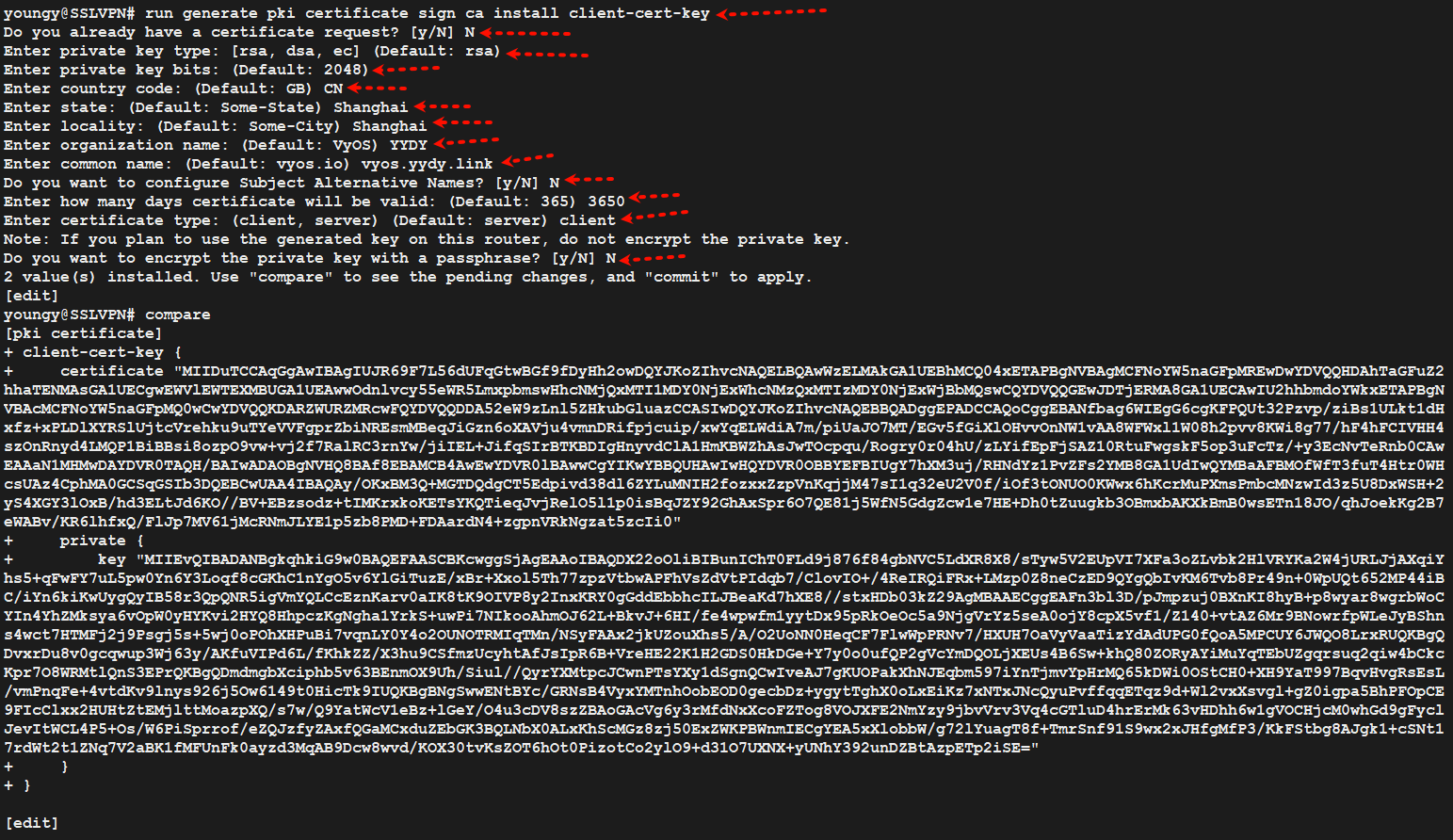
4.4、生成客户端证书和密钥
run generate pki certificate sign ca install client-cert-key
4.5、配置openvpn接口
set interfaces openvpn vtun5500 description 'OpenVPN-Server'
set interfaces openvpn vtun5500 encryption data-ciphers 'aes256'
set interfaces openvpn vtun5500 hash 'sha512'
set interfaces openvpn vtun5500 local-host '10.225.97.8'
set interfaces openvpn vtun5500 local-port '5500'
set interfaces openvpn vtun5500 mode 'server'
set interfaces openvpn vtun5500 openvpn-option '--script-security 3'
set interfaces openvpn vtun5500 openvpn-option '--persist-key'
set interfaces openvpn vtun5500 openvpn-option '--persist-tun'
set interfaces openvpn vtun5500 openvpn-option '--duplicate-cn'
set interfaces openvpn vtun5500 openvpn-option '--push redirect-gateway'
set interfaces openvpn vtun5500 openvpn-option '--auth-user-pass-verify /config/auth/checkpsw.sh via-env'
set interfaces openvpn vtun5500 openvpn-option '--username-as-common-name'
set interfaces openvpn vtun5500 persistent-tunnel
set interfaces openvpn vtun5500 protocol 'udp'
set interfaces openvpn vtun5500 server client-ip-pool start '100.64.168.2'
set interfaces openvpn vtun5500 server client-ip-pool stop '100.64.168.254'
set interfaces openvpn vtun5500 server client-ip-pool subnet-mask '255.255.255.0'
set interfaces openvpn vtun5500 server domain-name 'vyos.yydy.link'
set interfaces openvpn vtun5500 server max-connections '250'
set interfaces openvpn vtun5500 server name-server '223.5.5.5'
set interfaces openvpn vtun5500 server name-server '223.6.6.6'
set interfaces openvpn vtun5500 server subnet '100.64.168.0/24'
set interfaces openvpn vtun5500 server topology 'subnet'
set interfaces openvpn vtun5500 tls ca-certificate 'ca'
set interfaces openvpn vtun5500 tls certificate 'server-cert-key'
set interfaces openvpn vtun5500 tls dh-params 'dh'
set interfaces openvpn vtun5500 use-lzo-compression
set interfaces openvpn vtun5500 description 'OpenVPN-Server'
- 描述:为 OpenVPN 接口
vtun5500设置一个描述性名称,这样可以方便后续的管理和识别。 - 作用:在配置输出和管理界面中显示这个接口的描述。
set interfaces openvpn vtun5500 encryption data-ciphers 'aes256'
- 描述:设置 OpenVPN 连接的数据加密算法。
- 作用:这里指定加密算法
aes256,提供 256 位的 AES 加密,以增强数据安全性。
set interfaces openvpn vtun5500 hash 'sha512'
- 描述:设置 OpenVPN 连接的哈希算法。
- 作用:指定使用
sha512作为数据认证和验证的哈希算法。相比于sha1和md5,sha512提供更高的安全性。
set interfaces openvpn vtun5500 local-host '10.225.97.8'
- 描述:设置 OpenVPN 服务器的本地 IP 地址。
- 作用:指定 OpenVPN 服务监听的本地 IP 地址,这个地址将作为客户端连接到 OpenVPN 服务器的源 IP。
set interfaces openvpn vtun5500 local-port '5500'
- 描述:设置 OpenVPN 服务器监听的本地端口。
- 作用:指定 OpenVPN 服务监听的端口(
5500),客户端连接到这个端口来建立 OpenVPN 连接。
set interfaces openvpn vtun5500 mode 'server'
- 描述:设置 OpenVPN 模式为
server。 - 作用:启用 OpenVPN 服务器模式,这样客户端可以通过服务器与 OpenVPN 网段通信。
set interfaces openvpn vtun5500 openvpn-option '--script-security 3'
- 描述:设置 OpenVPN 脚本安全级别。
- 作用:脚本安全级别
3表示允许脚本从 OpenVPN 服务读取环境变量和调用外部脚本,但不允许直接调用脚本脚本。
set interfaces openvpn vtun5500 openvpn-option '--persist-key'
- 描述:设置 OpenVPN 客户端和服务器之间的持久密钥。
- 作用:保持密钥即使重启也不会丢失。
set interfaces openvpn vtun5500 openvpn-option '--persist-tun'
- 描述:设置 OpenVPN 客户端和服务器之间的持久网桥。
- 作用:保持 VPN 隧道即使重启也不会丢失。
set interfaces openvpn vtun5500 openvpn-option '--comp-lzo'
- 描述:启用 LZO 压缩。
- 作用:启用数据流量压缩,可以提高数据传输速度,但影响安全性。
set interfaces openvpn vtun5500 openvpn-option '--duplicate-cn'
- 描述:允许一个客户端同时拥有多个 OpenVPN 连接。
- 作用:支持同一用户多连接。
set interfaces openvpn vtun5500 openvpn-option '--push redirect-gateway'
- 描述:推送重定向网关选项。
- 作用:在客户端连接时,自动将所有流量通过 VPN 通道转发到服务器。
set interfaces openvpn vtun5500 openvpn-option '--auth-user-pass-verify /config/auth/checkpsw.sh via-env'
- 描述:验证用户凭据的脚本路径。
- 作用:设置用户验证脚本,用于验证用户名和密码。
set interfaces openvpn vtun5500 openvpn-option '--username-as-common-name'
- 描述:使用用户名作为 OpenVPN 公用名称。
- 作用:通过客户端的用户名来生成公用名称。
set interfaces openvpn vtun5500 persistent-tunnel
- 描述:设置 OpenVPN 的持久性隧道。
- 作用:确保连接即使在网络中断情况下也不会丢失。
set interfaces openvpn vtun5500 protocol 'udp'
- 描述:设置 OpenVPN 协议。
- 作用:使用
udp协议可以支持更高的流量处理和较低的延迟,但稳定性稍差于tcp。
set interfaces openvpn vtun5500 server client-ip-pool start '100.64.168.2'
- 描述:设置 OpenVPN 客户端 IP 池的起始地址。
- 作用:指定客户端的 IP 地址池范围的起始地址。
set interfaces openvpn vtun5500 server client-ip-pool stop '100.64.168.254'
- 描述:设置 OpenVPN 客户端 IP 池的结束地址。
- 作用:指定客户端的 IP 地址池范围的结束地址。
set interfaces openvpn vtun5500 server client-ip-pool subnet-mask '255.255.255.0'
- 描述:设置 OpenVPN 客户端 IP 池的子网掩码。
- 作用:指定客户端 IP 地址池的子网掩码。
set interfaces openvpn vtun5500 server domain-name 'vyos.yydy.link'
- 描述:设置 OpenVPN 服务器的域名。
- 作用:通过这个域名可以方便访问客户端连接。
set interfaces openvpn vtun5500 server max-connections '250'
- 描述:设置 OpenVPN 服务器的最大连接数。
- 作用:限制同时允许的客户端连接数。
set interfaces openvpn vtun5500 server name-server '223.5.5.5'
- 描述:设置 OpenVPN 服务器的 DNS 服务器。
- 作用:为客户端提供 DNS 服务,允许客户端通过 VPN 使用特定 DNS 服务器。
set interfaces openvpn vtun5500 server name-server '223.6.6.6'
- 描述:设置第二个 OpenVPN 服务器的 DNS 服务器。
- 作用:如果第一个 DNS 服务器不可用,则使用备用 DNS 服务器。
set interfaces openvpn vtun5500 server subnet '100.64.168.0/24'
- 描述:设置 OpenVPN 服务器的子网。
- 作用:定义客户端 IP 地址的网络范围。
set interfaces openvpn vtun5500 server topology 'subnet'
- 描述:设置 OpenVPN 的拓扑结构。
- 作用:选择
subnet选项,使客户端通过 VPN 可以访问整个子网。
set interfaces openvpn vtun5500 tls ca-certificate 'ca'
- 描述:设置 OpenVPN 服务器的 CA 证书。
- 作用:为 OpenVPN 服务提供证书认证,验证客户端和服务器的身份。
set interfaces openvpn vtun5500 tls certificate 'server-cert-key'
- 描述:设置 OpenVPN 服务器的证书和密钥。
- 作用:用于身份验证 OpenVPN 服务器。
set interfaces openvpn vtun5500 tls dh-params 'dh'
- 描述:设置 OpenVPN Diffie-Hellman 参数。
- 作用:增强 OpenVPN 连接的加密安全性。
set interfaces openvpn vtun5500 use-lzo-compression
- 描述:启用 LZO 压缩。
- 作用:减少数据包大小,提高数据传输效率,但可能对数据安全性产生影响。
五、创建用户名密码验证脚本
5.1、创建checkpsw.sh
sudo nano /config/auth/checkpsw.sh
#!/bin/sh
###########################################################
# checkpsw.sh (C) 2004 Mathias Sundman <mathias@openvpn.se>
#
# This script will authenticate OpenVPN users against
# a plain text file. The passfile should simply contain
# one row per user with the username first followed by
# one or more space(s) or tab(s) and then the password.
###########################################################
PASSFILE="/config/auth/openvpn_user_passwd.txt"
LOG_FILE="/config/auth/openvpn.log"
TIME_STAMP=`date "+%Y-%m-%d %T"`
if [ ! -r "${PASSFILE}" ]; then
echo "${TIME_STAMP}: Could not open password file \"${PASSFILE}\" for reading." >> ${LOG_FILE}
exit 1
fi
CORRECT_PASSWORD=`awk '!/^;/&&!/^#/&&$1=="'${username}'"{print $2;exit}' ${PASSFILE}`
if [ "${CORRECT_PASSWORD}" = "" ]; then
echo "${TIME_STAMP}: User does not exist: username=\"${username}\", password=\"${password}\"." >> ${LOG_FILE}
exit 1
fi
if [ "${password}" = "${CORRECT_PASSWORD}" ]; then
echo "${TIME_STAMP}: Successful authentication: username=\"${username}\"." >> ${LOG_FILE}
exit 0
fi
echo "${TIME_STAMP}: Incorrect password: username=\"${username}\", password=\"${password}\"." >> ${LOG_FILE}
exit 1
5.2、赋权checkpsw.sh
sudo chmod +x /config/auth/checkpsw.sh
5.3、创建密码本
sudo nano /config/auth/openvpn_user_passwd.txt
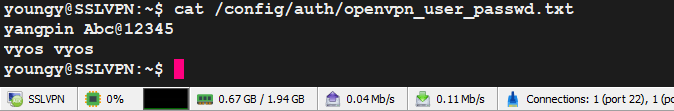
5.4、赋权密码本
sudo chmod 664 /config/auth/openvpn_user_passwd.txt
5.5、创建拨号日志文件
sudo nano /config/auth/openvpn.log
六、生成客户端配置
6.1、创建生成移动端配置脚本
sudo nano vyos_ovpn.sh
6.2、贴入配置
#!/bin/vbash
source /opt/vyatta/etc/functions/script-template
# 输出配置文件的名称
OUTPUT_FILE="vyos.ovpn"
# 提取服务器的配置
SERVER_IP=$(run show conf com | grep "vtun" | grep "local-host" | awk -F"'" '{print $2}')
PORT=$(run show conf com | grep "vtun" | grep "local-port" | awk -F"'" '{print $2}')
PROTOCOL=$(run show conf com | grep "vtun" | grep "protocol" | awk -F"'" '{print $2}')
# 提取证书和密钥内容
CA_CERT=$(run show conf com | grep "ca ca certificate" | awk -F"'" '{print $2}')
CLIENT_CERT=$(run show conf com | grep "client-cert-key certificate" | awk -F"'" '{print $2}')
CLIENT_KEY=$(run show conf com | grep "client-cert-key private key" | awk -F"'" '{print $2}')
# 检查是否成功提取证书和密钥内容
if [[ -z "$CA_CERT" || -z "$CLIENT_CERT" || -z "$CLIENT_KEY" ]]; then
echo "Error: Unable to fetch certificate or key information from VyOS configuration."
exit 1
fi
# 格式化证书内容,每行限制为64个字符
format_cert() {
echo "$1" | fold -w 64
}
# 写入OpenVPN配置文件
cat > $OUTPUT_FILE <<EOF
setenv FRIENDLY_NAME "VyOS SSL VPN"
client
dev tun
proto $PROTOCOL
remote $SERVER_IP $PORT
resolv-retry infinite
auth-user-pass
nobind
persist-key
persist-tun
remote-cert-tls server
comp-lzo
auth SHA512
cipher AES-256-CBC
verb 3
key-direction 1
<ca>
-----BEGIN CERTIFICATE-----
$(format_cert "$CA_CERT")
-----END CERTIFICATE-----
</ca>
<cert>
-----BEGIN CERTIFICATE-----
$(format_cert "$CLIENT_CERT")
-----END CERTIFICATE-----
</cert>
<key>
-----BEGIN PRIVATE KEY-----
$(format_cert "$CLIENT_KEY")
-----END PRIVATE KEY-----
</key>
EOF
echo "OpenVPN configuration file '$OUTPUT_FILE' has been created successfully."
6.3、赋权vyos_ovpn.sh
sudo chmod +x vyos_ovpn.sh
6.4、执行脚本获取vyos.ovpn
sudo bash vyos_ovpn.sh
6.5、移动终端配置文件
setenv FRIENDLY_NAME "VyOS SSL VPN"
client
dev tun
proto udp
remote 10.225.97.8 5500
resolv-retry infinite
auth-user-pass
nobind
persist-key
persist-tun
remote-cert-tls server
comp-lzo
auth SHA512
cipher AES-256-CBC
verb 3
key-direction 1
<ca>
-----BEGIN CERTIFICATE-----
MIIDpTCCAo2gAwIBAgIUKHUwAKo2gAHcS0CodBC+NcHrolYwDQYJKoZIhvcNAQEL
BQAwWzELMAkGA1UEBhMCQ04xETAPBgNVBAgMCFNoYW5naGFpMREwDwYDVQQHDAhT
aGFuZ2hhaTENMAsGA1UECgwEWVlEWTEXMBUGA1UEAwwOdnlvcy55eWR5Lmxpbmsw
HhcNMjQxMTI1MDYzMDUwWhcNMzQxMTIzMDYzMDUwWjBbMQswCQYDVQQGEwJDTjER
MA8GA1UECAwIU2hhbmdoYWkxETAPBgNVBAcMCFNoYW5naGFpMQ0wCwYDVQQKDARZ
WURZMRcwFQYDVQQDDA52eW9zLnl5ZHkubGluazCCASIwDQYJKoZIhvcNAQEBBQAD
ggEPADCCAQoCggEBANz5xJjmAD1OH4jJT2PsK0DjlGn9b55sVaE0DYo3aDAN6HL3
HuQTvNYL4pCZB+rzhLvrL69BB9rTm9iZnTckCGBfva2Ike0KTpXpXG30D3HeEBtC
5LPa6IaLBQAsyXbBrC00yA0xoeG2wR51u272hAa6H+2tdDiwFeYLk2jFsK8YwPNa
Ij64vNEwBKUPJoNPrTgW7HQZ+6o7RDa5FPTZQyMhHm92q53AmsaBKwLmnzhuVD56
eMX51rgNHxHwiy+lhe34pFoC6lo/HHUCKN2AdRy+Ae8BehjZ2Oq3begg5QAuNZh0
5O+hGEDdKd/wwjLv/5eIKpaHiTyPPO0YMDJ8IJ0CAwEAAaNhMF8wDwYDVR0TAQH/
BAUwAwEB/zAOBgNVHQ8BAf8EBAMCAYYwHQYDVR0lBBYwFAYIKwYBBQUHAwIGCCsG
AQUFBwMBMB0GA1UdDgQWBBQTDn1n0937k+B7a9Fh3LFAM+AqYTANBgkqhkiG9w0B
AQsFAAOCAQEAALkUc566dAwy/4rdGs3v8jfV9zhWJLnh1vALE0k7NzkQ/UjebT2U
cooc4KTSZsssA50bF4ve22osm8Wo3RlKVZ1o/omzZzirfMByMuqriq4HrrhVbY9y
Xt//bCLqlZbWTSBne73zde9HIQgjnmQFrqyfXCKWOjdrCOQU8gr5PQ8n0oEaRpPg
Z8lPZxMy/5lWpWdWbnhXObyPzbweF8cmvugDuoNhk9wFq+4+EA22M84InX9UFvmB
DD0mATgba3c2lJaM9/NJHDF1HlrWqUwaeKCzA6YLuppYWmRRoLs8wyrZkhLV6HM4
2PogwqEzgDveEFFjpNLSuFOFm7PnB8i7ew==
-----END CERTIFICATE-----
</ca>
<cert>
-----BEGIN CERTIFICATE-----
MIIDuTCCAqGgAwIBAgIUJR69F7L56dUFqGtwBGf9fDyHh2owDQYJKoZIhvcNAQEL
BQAwWzELMAkGA1UEBhMCQ04xETAPBgNVBAgMCFNoYW5naGFpMREwDwYDVQQHDAhT
aGFuZ2hhaTENMAsGA1UECgwEWVlEWTEXMBUGA1UEAwwOdnlvcy55eWR5Lmxpbmsw
HhcNMjQxMTI1MDY0NjExWhcNMzQxMTIzMDY0NjExWjBbMQswCQYDVQQGEwJDTjER
MA8GA1UECAwIU2hhbmdoYWkxETAPBgNVBAcMCFNoYW5naGFpMQ0wCwYDVQQKDARZ
WURZMRcwFQYDVQQDDA52eW9zLnl5ZHkubGluazCCASIwDQYJKoZIhvcNAQEBBQAD
ggEPADCCAQoCggEBANfbag6WIEgG6cgKFPQUt32Pzvp/ziBs1ULkt1dHxfz+xPLD
lXYRSlUjtcVrehku9uTYeVVFgprZbiNREsmMBeqJiGzn6oXAVju4vmnDRifpjcui
p/xwYqELWdiA7m/piUaJO7MT/EGv5fGiXlOHvvOnNW1vAA8WFWxl1W08h2pvv8KW
i8g77/hF4hFCIVHH4szOnRnyd4LMQP1BiBBsi8ozpO9vw+vj2f7RalRC3rnYw/ji
IEL+JifqSIrBTKBDIgHnyvdClA1HmKBWZhAsJwTOcpqu/Rogry0r04hU/zLYifEp
FjSAZ10RtuFwgskF5op3uFcTz/+y3EcNvTeRnb0CAwEAAaN1MHMwDAYDVR0TAQH/
BAIwADAOBgNVHQ8BAf8EBAMCB4AwEwYDVR0lBAwwCgYIKwYBBQUHAwIwHQYDVR0O
BBYEFBIUgY7hXM3uj/RHNdYz1PvZFs2YMB8GA1UdIwQYMBaAFBMOfWfT3fuT4Htr
0WHcsUAz4CphMA0GCSqGSIb3DQEBCwUAA4IBAQAy/OKxBM3Q+MGTDQdgCT5Edpiv
d38dl6ZYLuMNIH2fozxxZzpVnKqjjM47sI1q32eU2V0f/iOf3tONUO0KWwx6hKcr
MuPXmsPmbcMNzwId3z5U8DxWSH+2yS4XGY3lOxB/hd3ELtJd6KO//BV+EBzsodz+
tIMKrxkoKETsYKQTieqJvjRelO5l1p0isBqJZY92GhAxSpr6O7QE81j5WfN5GdgZ
cw1e7HE+Dh0tZuugkb3OBmxbAKXkBmB0wsETn18JO/qhJoekKg2B7eWABv/KR6lh
fxQ/FlJp7MV61jMcRNmJLYE1p5zb8PMD+FDAardN4+zgpnVRkNgzat5zcIi0
-----END CERTIFICATE-----
</cert>
<key>
-----BEGIN PRIVATE KEY-----
MIIEvQIBADANBgkqhkiG9w0BAQEFAASCBKcwggSjAgEAAoIBAQDX22oOliBIBunI
ChT0FLd9j876f84gbNVC5LdXR8X8/sTyw5V2EUpVI7XFa3oZLvbk2HlVRYKa2W4j
URLJjAXqiYhs5+qFwFY7uL5pw0Yn6Y3Loqf8cGKhC1nYgO5v6YlGiTuzE/xBr+Xx
ol5Th77zpzVtbwAPFhVsZdVtPIdqb7/ClovIO+/4ReIRQiFRx+LMzp0Z8neCzED9
QYgQbIvKM6Tvb8Pr49n+0WpUQt652MP44iBC/iYn6kiKwUygQyIB58r3QpQNR5ig
VmYQLCcEznKarv0aIK8tK9OIVP8y2InxKRY0gGddEbbhcILJBeaKd7hXE8//stxH
Db03kZ29AgMBAAECggEAFn3bl3D/pJmpzuj0BXnKI8hyB+p8wyar8wgrbWoCYIn4
YhZMksya6vOpW0yHYKvi2HYQ8HhpczKgNgha1YrkS+uwPi7NIkooAhmOJ62L+Bkv
J+6HI/fe4wpwfm1yytDx95pRkOeOc5a9NjgVrYz5seA0ojY8cpX5vf1/Z140+vtA
Z6Mr9BNowrfpWLeJyBShns4wct7HTMFj2j9Psgj5s+5wj0oPOhXHPuBi7vqnLY0Y
4o2OUNOTRMIqTMn/NSyFAAx2jkUZouXhs5/A/O2UoNN0HeqCF7FlwWpPRNv7/HXU
H7OaVyVaaTizYdAdUPG0fQoA5MPCUY6JWQO8LrxRUQKBgQDvxrDu8v0gcqwup3Wj
63y/AKfuVIPd6L/fKhkZZ/X3hu9CSfmzUcyhtAfJsIpR6B+VreHE22K1H2GDS0Hk
DGe+Y7y0o0ufQP2gVcYmDQOLjXEUs4B6Sw+khQ80ZORyAYiMuYqTEbUZgqrsuq2q
iw4bCkcKpr7O8WRMtlQnS3EPrQKBgQDmdmgbXciphb5v63BEnmOX9Uh/Siul//Qy
rYXMtpcJCwnPTsYXy1dSgnQCwIveAJ7gKUOPakXhNJEqbm597iYnTjmvYpHrMQ65
kDWi0OStCH0+XH9YaT997BqvHvgRsEsL/vmPnqFe+4vtdKv9lnys926j5Ow6149t
0HicTk9IUQKBgBNgSwwENtBYc/GRNsB4VyxYMTnhOobEOD0gecbDz+ygytTghX0o
LxEiKz7xNTxJNcQyuPvffqqETqz9d+Wl2vxXsvgl+gZ0igpa5BhPFOpCE9FIcClx
x2HUHtZtEMjlttMoazpXQ/s7w/Q9YatWcV1eBz+lGeY/O4u3cDV8szZBAoGAcVg6
y3rMfdNxXcoFZTog8VOJXFE2NmYzy9jbvVrv3Vq4cGTluD4hrErMk63vHDhh6w1g
VOCHjcM0whGd9gFyclJevItWCL4P5+Os/W6PiSprrof/eZQJzfyZAxfQGaMCxduZ
EbGK3BQLNbX0ALxKhScMGz8zj50ExZWKPBWnmIECgYEA5xXlobbW/g72lYuagT8f
+TmrSnf91S9wx2xJHfgMfP3/KkFStbg8AJgk1+cSNt17rdWt2t1ZNq7V2aBK1fMF
UnFk0ayzd3MqAB9Dcw8wvd/KOX30tvKsZOT6hOt0PizotCo2ylO9+d31O7UXNX+y
UNhY392unDZBtAzpETp2iSE=
-----END PRIVATE KEY-----
</key>
6.6、vyos客户端配置文件
set pki ca ca certificate 'MIIDpTCCAo2gAwIBAgIUKHUwAKo2gAHcS0CodBC+NcHrolYwDQYJKoZIhvcNAQELBQAwWzELMAkGA1UEBhMCQ04xETAPBgNVBAgMCFNoYW5naGFpMREwDwYDVQQHDAhTaGFuZ2hhaTENMAsGA1UECgwEWVlEWTEXMBUGA1UEAwwOdnlvcy55eWR5LmxpbmswHhcNMjQxMTI1MDYzMDUwWhcNMzQxMTIzMDYzMDUwWjBbMQswCQYDVQQGEwJDTjERMA8GA1UECAwIU2hhbmdoYWkxETAPBgNVBAcMCFNoYW5naGFpMQ0wCwYDVQQKDARZWURZMRcwFQYDVQQDDA52eW9zLnl5ZHkubGluazCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBANz5xJjmAD1OH4jJT2PsK0DjlGn9b55sVaE0DYo3aDAN6HL3HuQTvNYL4pCZB+rzhLvrL69BB9rTm9iZnTckCGBfva2Ike0KTpXpXG30D3HeEBtC5LPa6IaLBQAsyXbBrC00yA0xoeG2wR51u272hAa6H+2tdDiwFeYLk2jFsK8YwPNaIj64vNEwBKUPJoNPrTgW7HQZ+6o7RDa5FPTZQyMhHm92q53AmsaBKwLmnzhuVD56eMX51rgNHxHwiy+lhe34pFoC6lo/HHUCKN2AdRy+Ae8BehjZ2Oq3begg5QAuNZh05O+hGEDdKd/wwjLv/5eIKpaHiTyPPO0YMDJ8IJ0CAwEAAaNhMF8wDwYDVR0TAQH/BAUwAwEB/zAOBgNVHQ8BAf8EBAMCAYYwHQYDVR0lBBYwFAYIKwYBBQUHAwIGCCsGAQUFBwMBMB0GA1UdDgQWBBQTDn1n0937k+B7a9Fh3LFAM+AqYTANBgkqhkiG9w0BAQsFAAOCAQEAALkUc566dAwy/4rdGs3v8jfV9zhWJLnh1vALE0k7NzkQ/UjebT2Ucooc4KTSZsssA50bF4ve22osm8Wo3RlKVZ1o/omzZzirfMByMuqriq4HrrhVbY9yXt//bCLqlZbWTSBne73zde9HIQgjnmQFrqyfXCKWOjdrCOQU8gr5PQ8n0oEaRpPgZ8lPZxMy/5lWpWdWbnhXObyPzbweF8cmvugDuoNhk9wFq+4+EA22M84InX9UFvmBDD0mATgba3c2lJaM9/NJHDF1HlrWqUwaeKCzA6YLuppYWmRRoLs8wyrZkhLV6HM42PogwqEzgDveEFFjpNLSuFOFm7PnB8i7ew=='
set pki certificate client-cert-key certificate 'MIIDuTCCAqGgAwIBAgIUJR69F7L56dUFqGtwBGf9fDyHh2owDQYJKoZIhvcNAQELBQAwWzELMAkGA1UEBhMCQ04xETAPBgNVBAgMCFNoYW5naGFpMREwDwYDVQQHDAhTaGFuZ2hhaTENMAsGA1UECgwEWVlEWTEXMBUGA1UEAwwOdnlvcy55eWR5LmxpbmswHhcNMjQxMTI1MDY0NjExWhcNMzQxMTIzMDY0NjExWjBbMQswCQYDVQQGEwJDTjERMA8GA1UECAwIU2hhbmdoYWkxETAPBgNVBAcMCFNoYW5naGFpMQ0wCwYDVQQKDARZWURZMRcwFQYDVQQDDA52eW9zLnl5ZHkubGluazCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBANfbag6WIEgG6cgKFPQUt32Pzvp/ziBs1ULkt1dHxfz+xPLDlXYRSlUjtcVrehku9uTYeVVFgprZbiNREsmMBeqJiGzn6oXAVju4vmnDRifpjcuip/xwYqELWdiA7m/piUaJO7MT/EGv5fGiXlOHvvOnNW1vAA8WFWxl1W08h2pvv8KWi8g77/hF4hFCIVHH4szOnRnyd4LMQP1BiBBsi8ozpO9vw+vj2f7RalRC3rnYw/jiIEL+JifqSIrBTKBDIgHnyvdClA1HmKBWZhAsJwTOcpqu/Rogry0r04hU/zLYifEpFjSAZ10RtuFwgskF5op3uFcTz/+y3EcNvTeRnb0CAwEAAaN1MHMwDAYDVR0TAQH/BAIwADAOBgNVHQ8BAf8EBAMCB4AwEwYDVR0lBAwwCgYIKwYBBQUHAwIwHQYDVR0OBBYEFBIUgY7hXM3uj/RHNdYz1PvZFs2YMB8GA1UdIwQYMBaAFBMOfWfT3fuT4Htr0WHcsUAz4CphMA0GCSqGSIb3DQEBCwUAA4IBAQAy/OKxBM3Q+MGTDQdgCT5Edpivd38dl6ZYLuMNIH2fozxxZzpVnKqjjM47sI1q32eU2V0f/iOf3tONUO0KWwx6hKcrMuPXmsPmbcMNzwId3z5U8DxWSH+2yS4XGY3lOxB/hd3ELtJd6KO//BV+EBzsodz+tIMKrxkoKETsYKQTieqJvjRelO5l1p0isBqJZY92GhAxSpr6O7QE81j5WfN5GdgZcw1e7HE+Dh0tZuugkb3OBmxbAKXkBmB0wsETn18JO/qhJoekKg2B7eWABv/KR6lhfxQ/FlJp7MV61jMcRNmJLYE1p5zb8PMD+FDAardN4+zgpnVRkNgzat5zcIi0'
set pki certificate client-cert-key private key 'MIIEvQIBADANBgkqhkiG9w0BAQEFAASCBKcwggSjAgEAAoIBAQDX22oOliBIBunIChT0FLd9j876f84gbNVC5LdXR8X8/sTyw5V2EUpVI7XFa3oZLvbk2HlVRYKa2W4jURLJjAXqiYhs5+qFwFY7uL5pw0Yn6Y3Loqf8cGKhC1nYgO5v6YlGiTuzE/xBr+Xxol5Th77zpzVtbwAPFhVsZdVtPIdqb7/ClovIO+/4ReIRQiFRx+LMzp0Z8neCzED9QYgQbIvKM6Tvb8Pr49n+0WpUQt652MP44iBC/iYn6kiKwUygQyIB58r3QpQNR5igVmYQLCcEznKarv0aIK8tK9OIVP8y2InxKRY0gGddEbbhcILJBeaKd7hXE8//stxHDb03kZ29AgMBAAECggEAFn3bl3D/pJmpzuj0BXnKI8hyB+p8wyar8wgrbWoCYIn4YhZMksya6vOpW0yHYKvi2HYQ8HhpczKgNgha1YrkS+uwPi7NIkooAhmOJ62L+BkvJ+6HI/fe4wpwfm1yytDx95pRkOeOc5a9NjgVrYz5seA0ojY8cpX5vf1/Z140+vtAZ6Mr9BNowrfpWLeJyBShns4wct7HTMFj2j9Psgj5s+5wj0oPOhXHPuBi7vqnLY0Y4o2OUNOTRMIqTMn/NSyFAAx2jkUZouXhs5/A/O2UoNN0HeqCF7FlwWpPRNv7/HXUH7OaVyVaaTizYdAdUPG0fQoA5MPCUY6JWQO8LrxRUQKBgQDvxrDu8v0gcqwup3Wj63y/AKfuVIPd6L/fKhkZZ/X3hu9CSfmzUcyhtAfJsIpR6B+VreHE22K1H2GDS0HkDGe+Y7y0o0ufQP2gVcYmDQOLjXEUs4B6Sw+khQ80ZORyAYiMuYqTEbUZgqrsuq2qiw4bCkcKpr7O8WRMtlQnS3EPrQKBgQDmdmgbXciphb5v63BEnmOX9Uh/Siul//QyrYXMtpcJCwnPTsYXy1dSgnQCwIveAJ7gKUOPakXhNJEqbm597iYnTjmvYpHrMQ65kDWi0OStCH0+XH9YaT997BqvHvgRsEsL/vmPnqFe+4vtdKv9lnys926j5Ow6149t0HicTk9IUQKBgBNgSwwENtBYc/GRNsB4VyxYMTnhOobEOD0gecbDz+ygytTghX0oLxEiKz7xNTxJNcQyuPvffqqETqz9d+Wl2vxXsvgl+gZ0igpa5BhPFOpCE9FIcClxx2HUHtZtEMjlttMoazpXQ/s7w/Q9YatWcV1eBz+lGeY/O4u3cDV8szZBAoGAcVg6y3rMfdNxXcoFZTog8VOJXFE2NmYzy9jbvVrv3Vq4cGTluD4hrErMk63vHDhh6w1gVOCHjcM0whGd9gFyclJevItWCL4P5+Os/W6PiSprrof/eZQJzfyZAxfQGaMCxduZEbGK3BQLNbX0ALxKhScMGz8zj50ExZWKPBWnmIECgYEA5xXlobbW/g72lYuagT8f+TmrSnf91S9wx2xJHfgMfP3/KkFStbg8AJgk1+cSNt17rdWt2t1ZNq7V2aBK1fMFUnFk0ayzd3MqAB9Dcw8wvd/KOX30tvKsZOT6hOt0PizotCo2ylO9+d31O7UXNX+yUNhY392unDZBtAzpETp2iSE='
set interfaces openvpn vtun5500 authentication password 'vyos'
set interfaces openvpn vtun5500 authentication username 'vyos'
set interfaces openvpn vtun5500 encryption data-ciphers 'aes256'
set interfaces openvpn vtun5500 hash 'sha512'
set interfaces openvpn vtun5500 mode 'client'
set interfaces openvpn vtun5500 persistent-tunnel
set interfaces openvpn vtun5500 protocol 'udp'
set interfaces openvpn vtun5500 remote-host '10.225.97.8'
set interfaces openvpn vtun5500 remote-port '5500'
set interfaces openvpn vtun5500 tls ca-certificate 'ca'
set interfaces openvpn vtun5500 tls certificate 'client-cert-key'
set interfaces openvpn vtun5500 use-lzo-compression
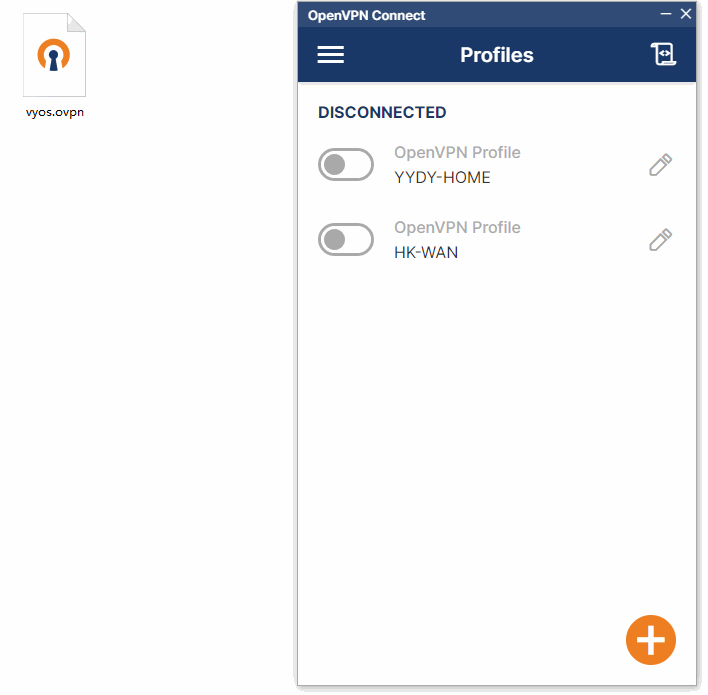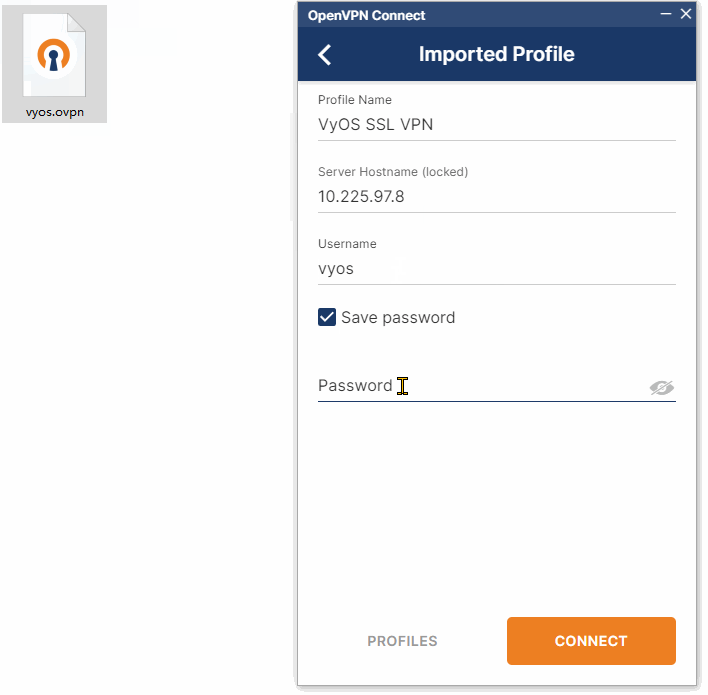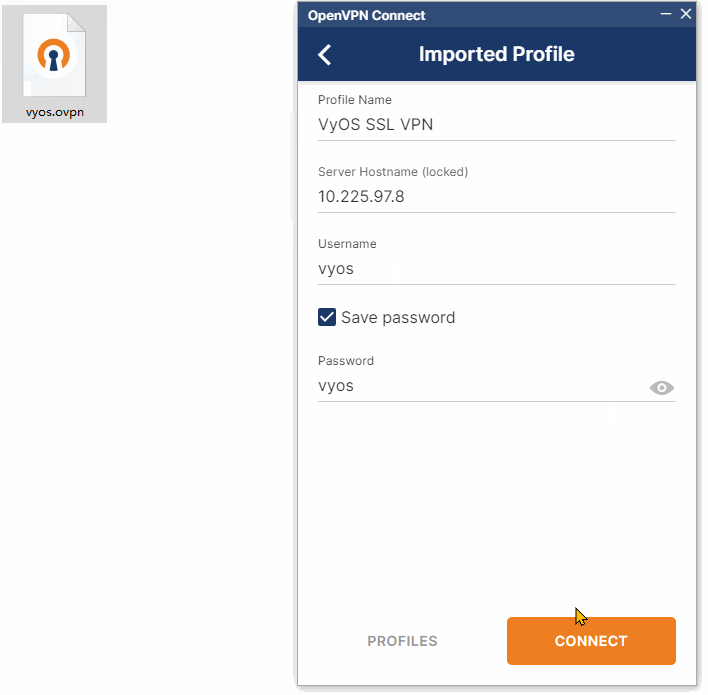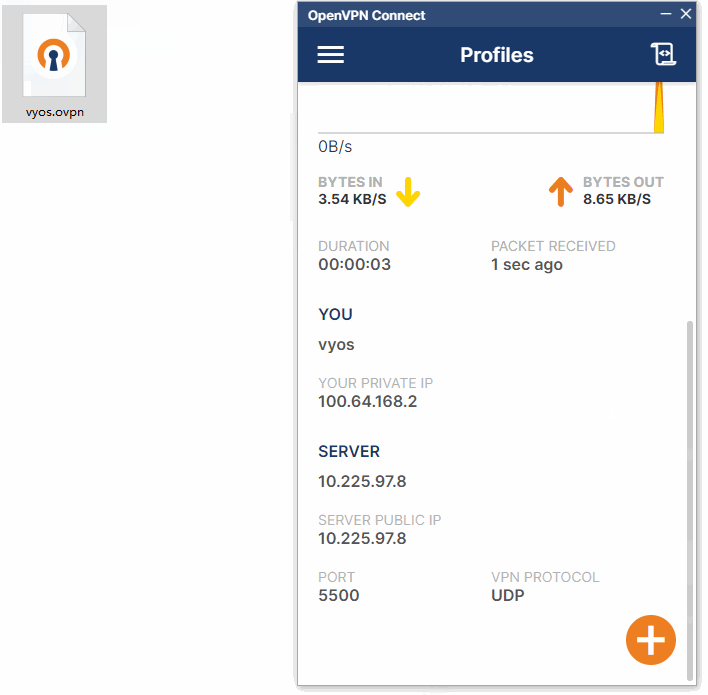
七、连接测试
7.1、windows连接测试
7.2、vyos客户端测试