文章介绍:本篇介绍使用vyos1.5官方滚动版部署OpenVPN Web GUI管理系统,支持在线编辑openvpn服务端配置,编辑openvpn客户端配置(企业版),创建CA和服务端证书(企业版),查看用户在线情况,批量添加用户,查看用户登录日志等功能。
一、项目来源
二、部署准备
2.1、vyos镜像
2.2、OpenVPN Web-GUI系统文件
2.3、OpenVPN客户端
三、安装vyos
3.1、VMware 安装 VyOS 指导
3.2、VyOS 基础配置指导
3.3、登录vyos
ssh -l vyos -p 22 10.225.97.9
3.4、vyos基础配置
configure
set interfaces ethernet eth0 address '10.225.97.9/24'
set nat destination rule 100 destination address '10.225.97.9'
set nat destination rule 100 destination port '80'
set nat destination rule 100 protocol 'tcp'
set nat destination rule 100 translation address '100.64.100.2'
set nat destination rule 100 translation port '80'
set nat destination rule 101 destination address '10.225.97.9'
set nat destination rule 101 destination port '1194'
set nat destination rule 101 protocol 'tcp_udp'
set nat destination rule 101 translation address '100.64.100.2'
set nat destination rule 101 translation port '1194'
set nat source rule 1000 outbound-interface name 'eth0'
set nat source rule 1000 translation address 'masquerade'
set protocols static route 0.0.0.0/0 next-hop 10.225.97.6
set service ssh disable-host-validation
set service ssh port '22'
set system host-name 'vyos'
set system login banner post-login 'VyOS OpenVPN Web GUI'
set system login user vyos authentication plaintext-password 'vyos'
set system name-server 10.225.97.6
commit
save
3.5、添加openvpn虚拟IP回程路由
set protocols static route 100.68.100.0/24 next-hop 100.64.100.2
commit
save
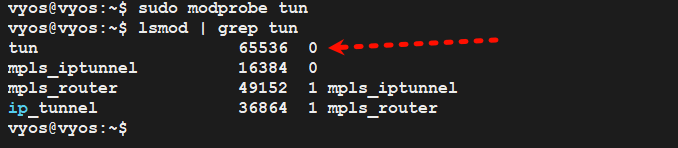
3.6、调优vyos参数
/etc/modules 文件,以便在系统启动时自动加载
sudo echo "tun" | sudo tee -a /etc/modules
sudo cat /etc/modules
sudo modprobe tun
sudo lsmod | grep tun
四、部署openvpn-web-gui
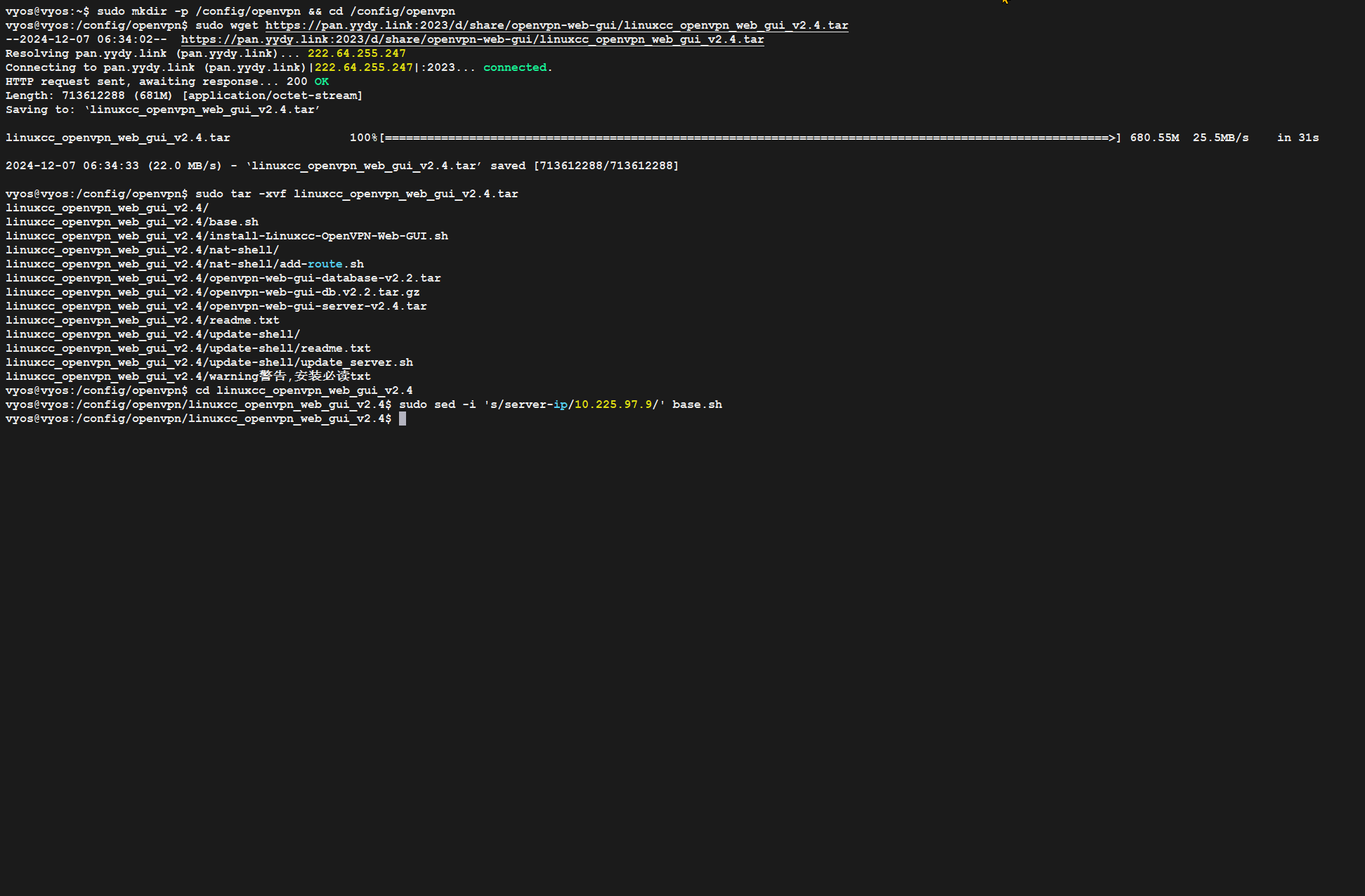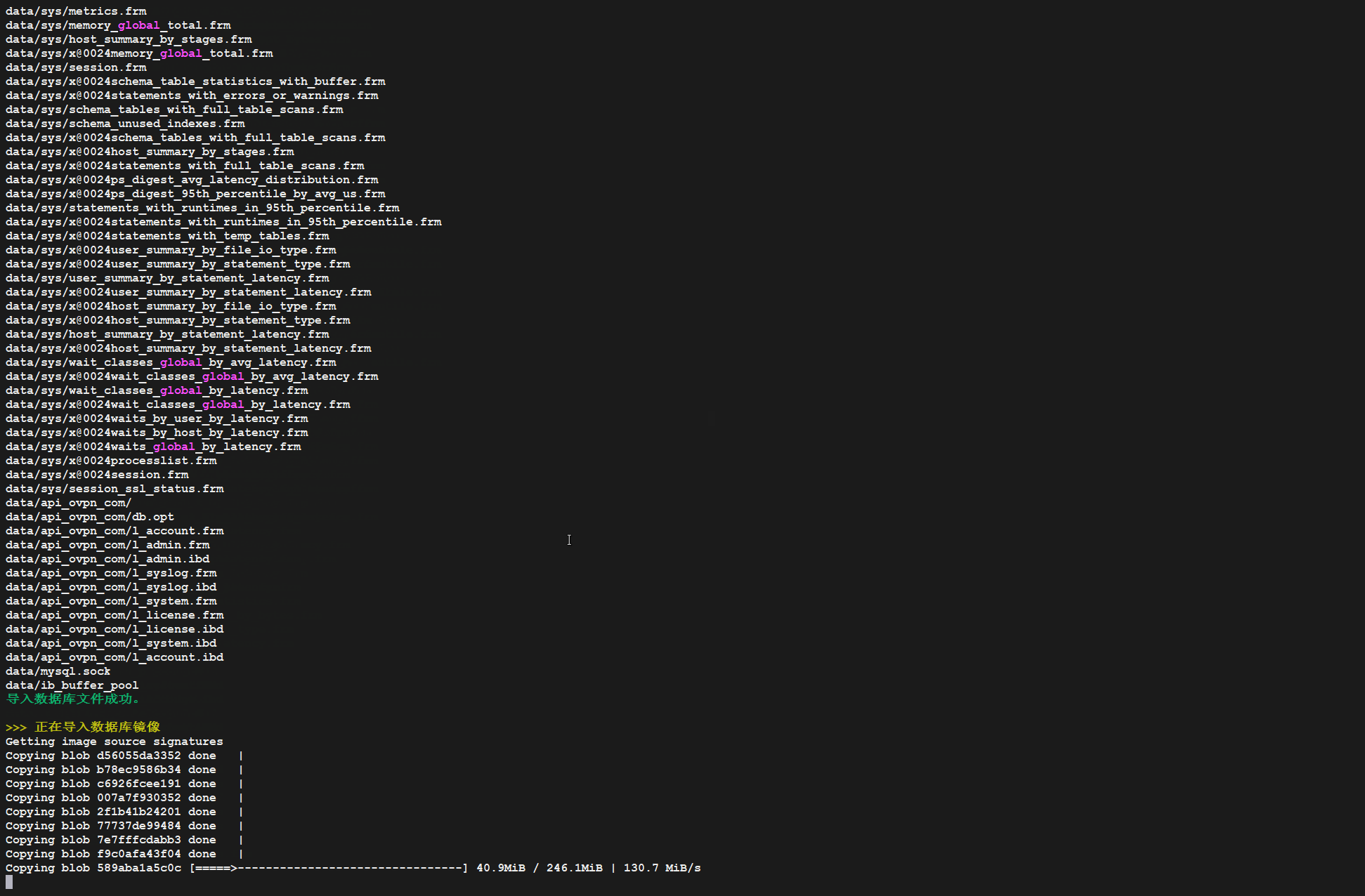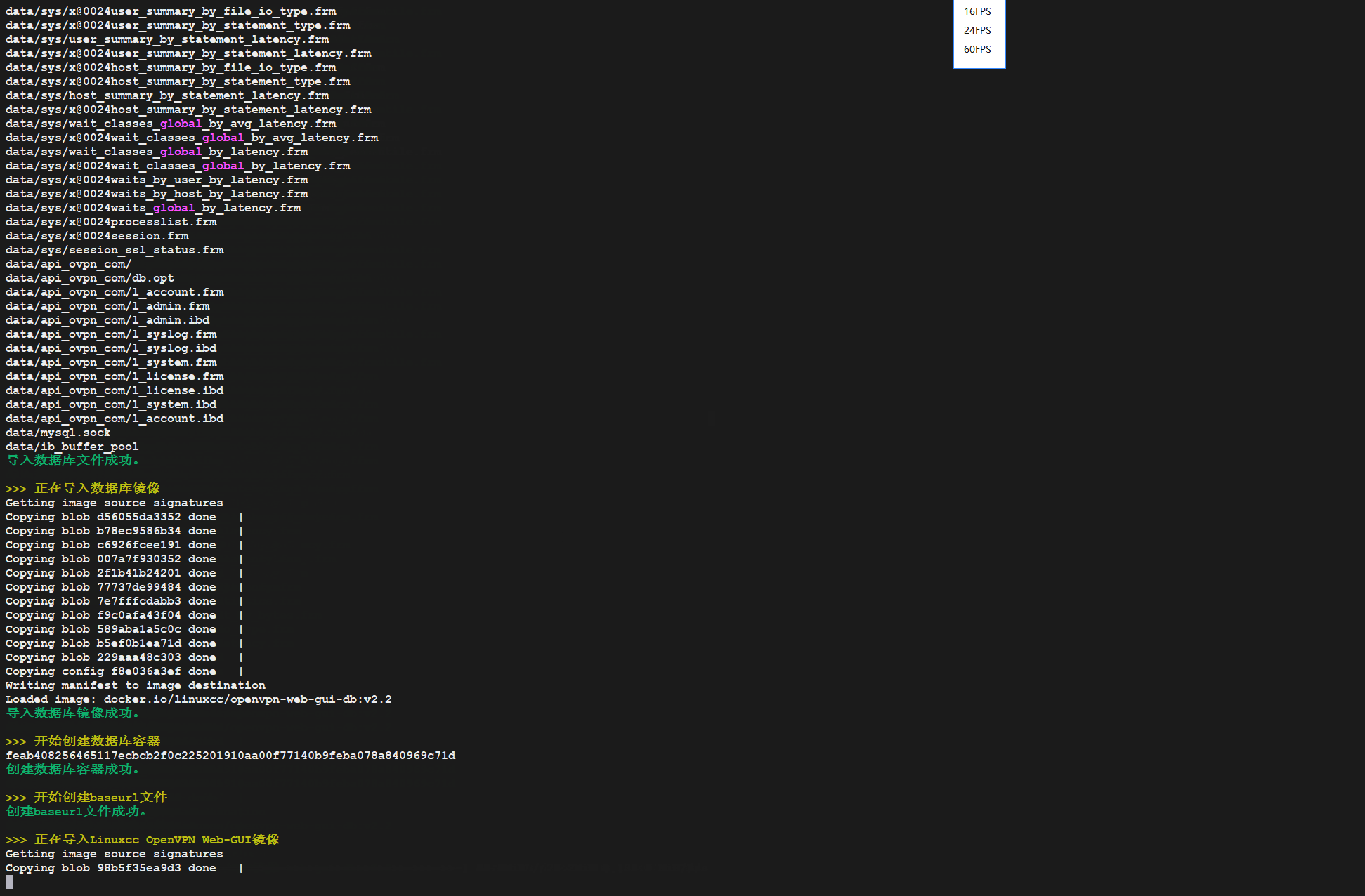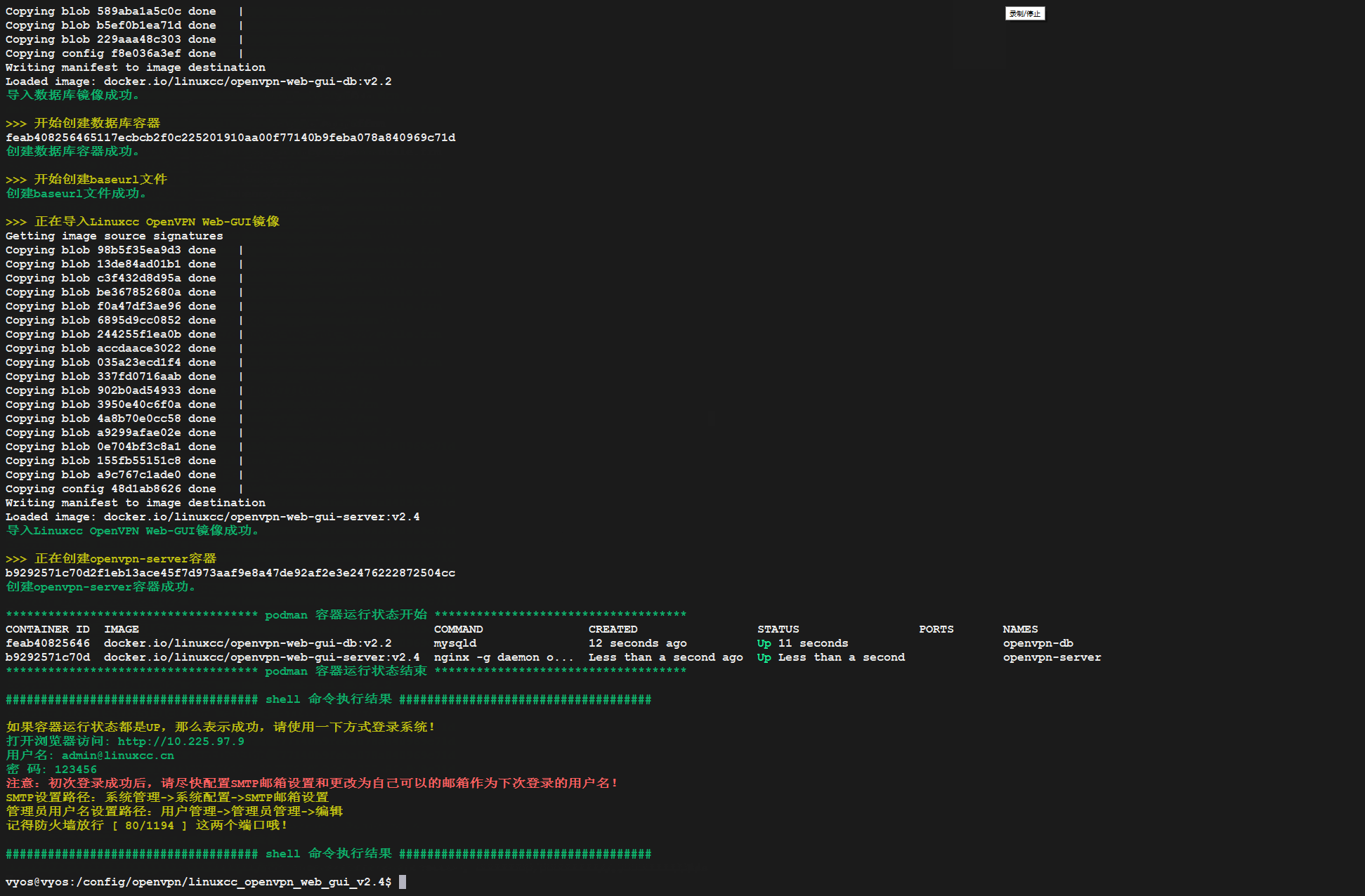
4.1、创建openvpn目录
sudo mkdir -p /config/openvpn && cd /config/openvpn
4.2、下载openvpn-web-gui系统文件
sudo wget https://pan.yydy.link:2023/d/share/openvpn/openvpn-web-gui/linuxcc_openvpn_web_gui_v2.4.tar
4.3、解压文件
sudo tar -xf linuxcc_openvpn_web_gui_v2.4.tar
4.4、进入配置目录
cd linuxcc_openvpn_web_gui_v2.4
4.5、修改bash.sh
sudo sed -i 's/server-ip/10.225.97.9/' base.sh
4.6、执行安装脚本
sudo bash install-Linuxcc-OpenVPN-Web-GUI.sh
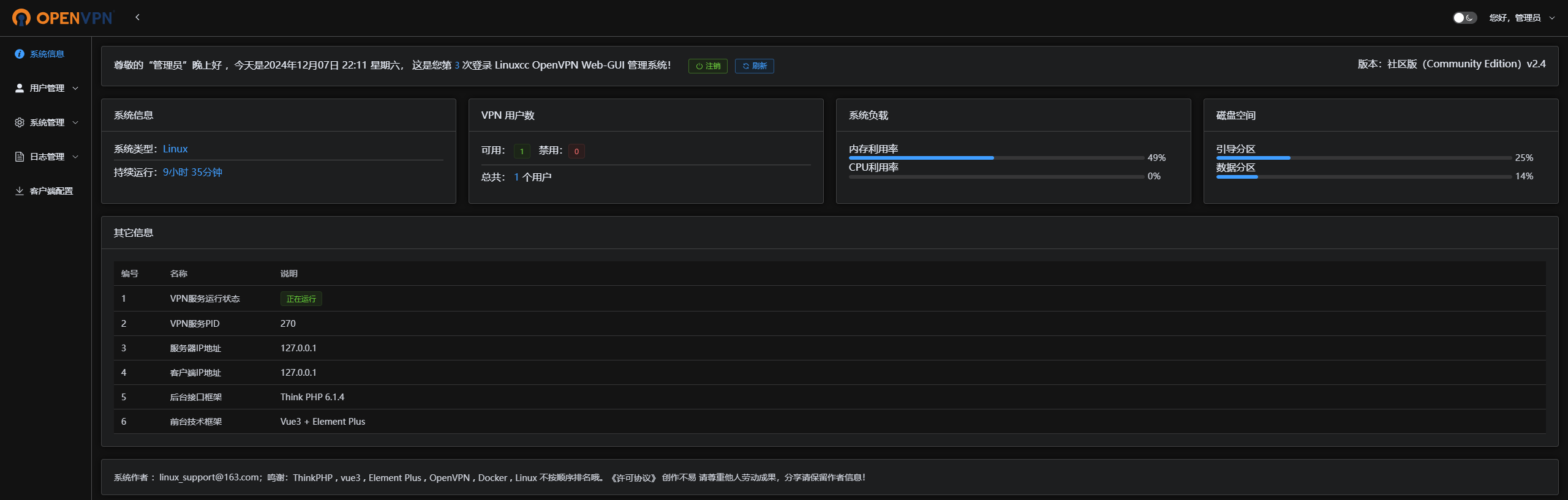
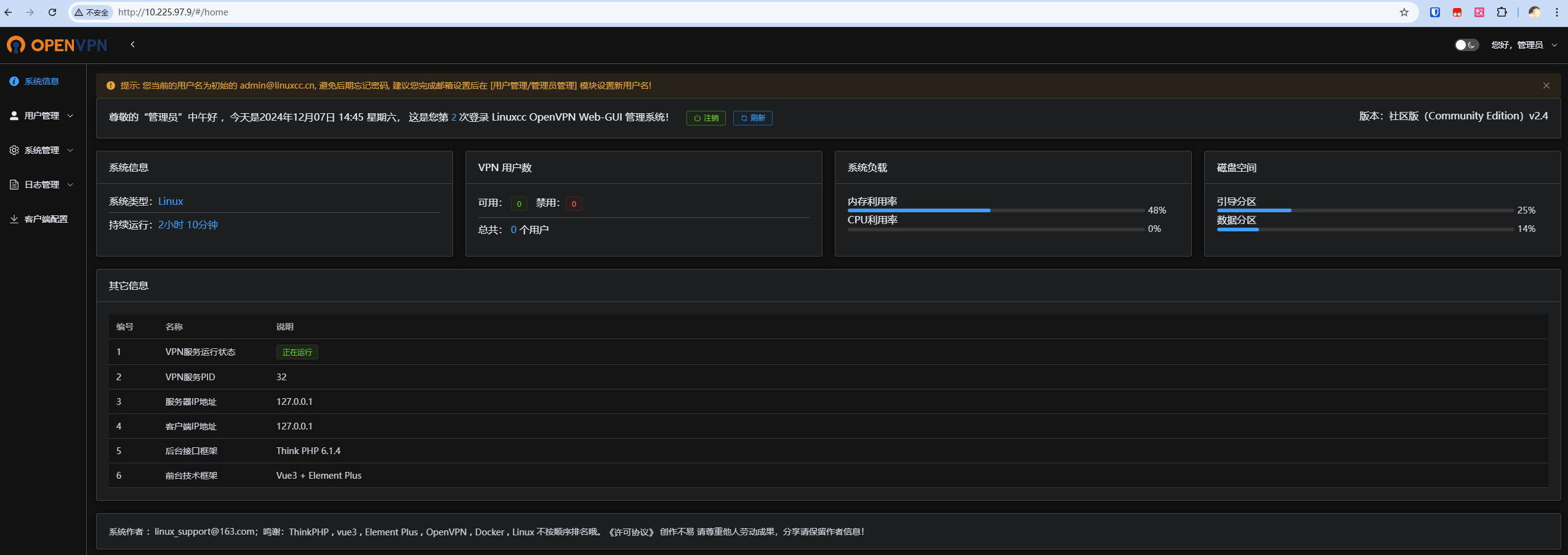
五、登录WEB-GUI
admin@linuxcc.cn
123456
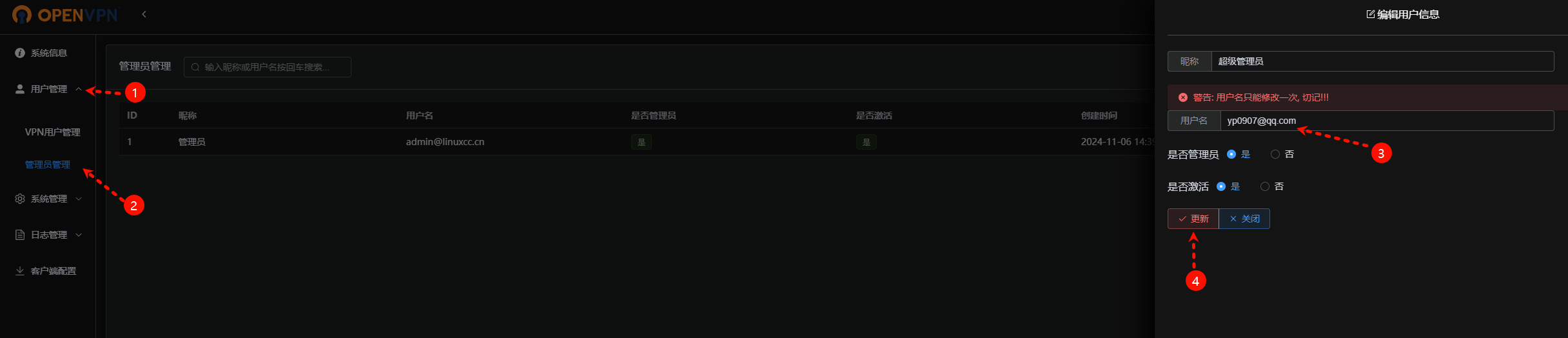
5.1、修改管理账号
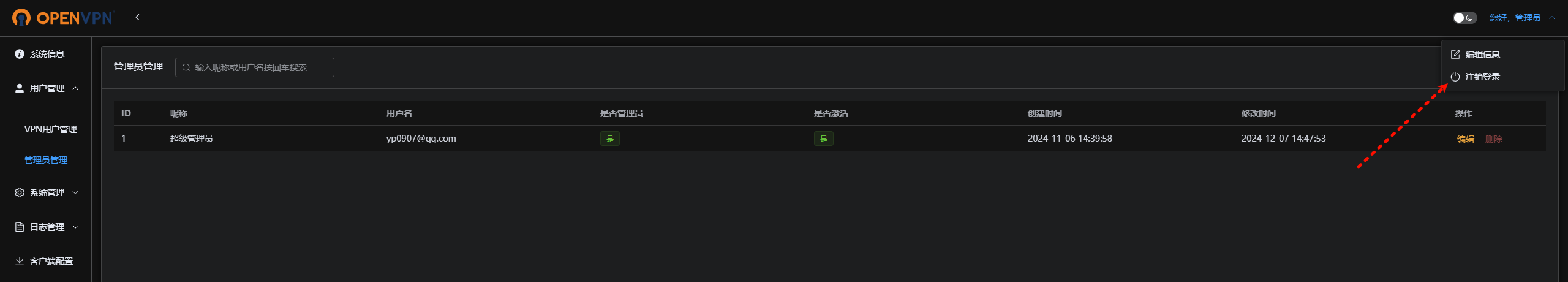
5.2、注销登录
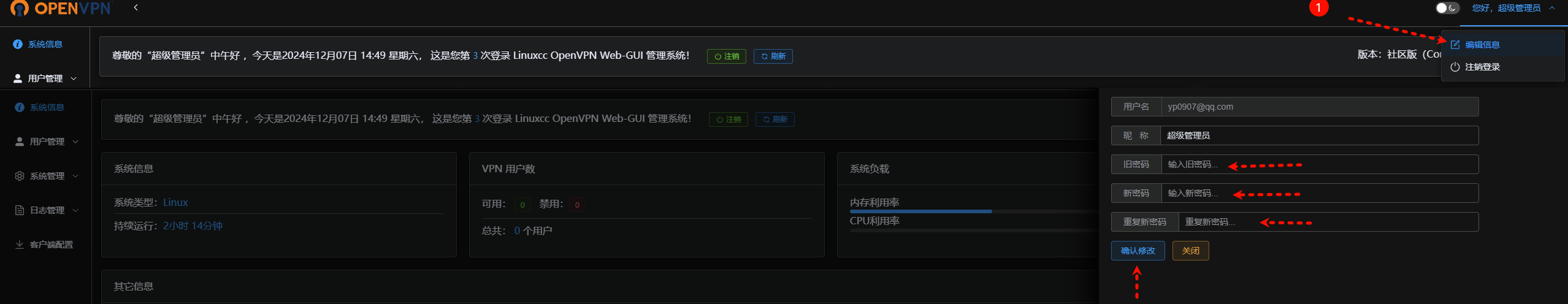
5.3、重新登录,修改管理员密码
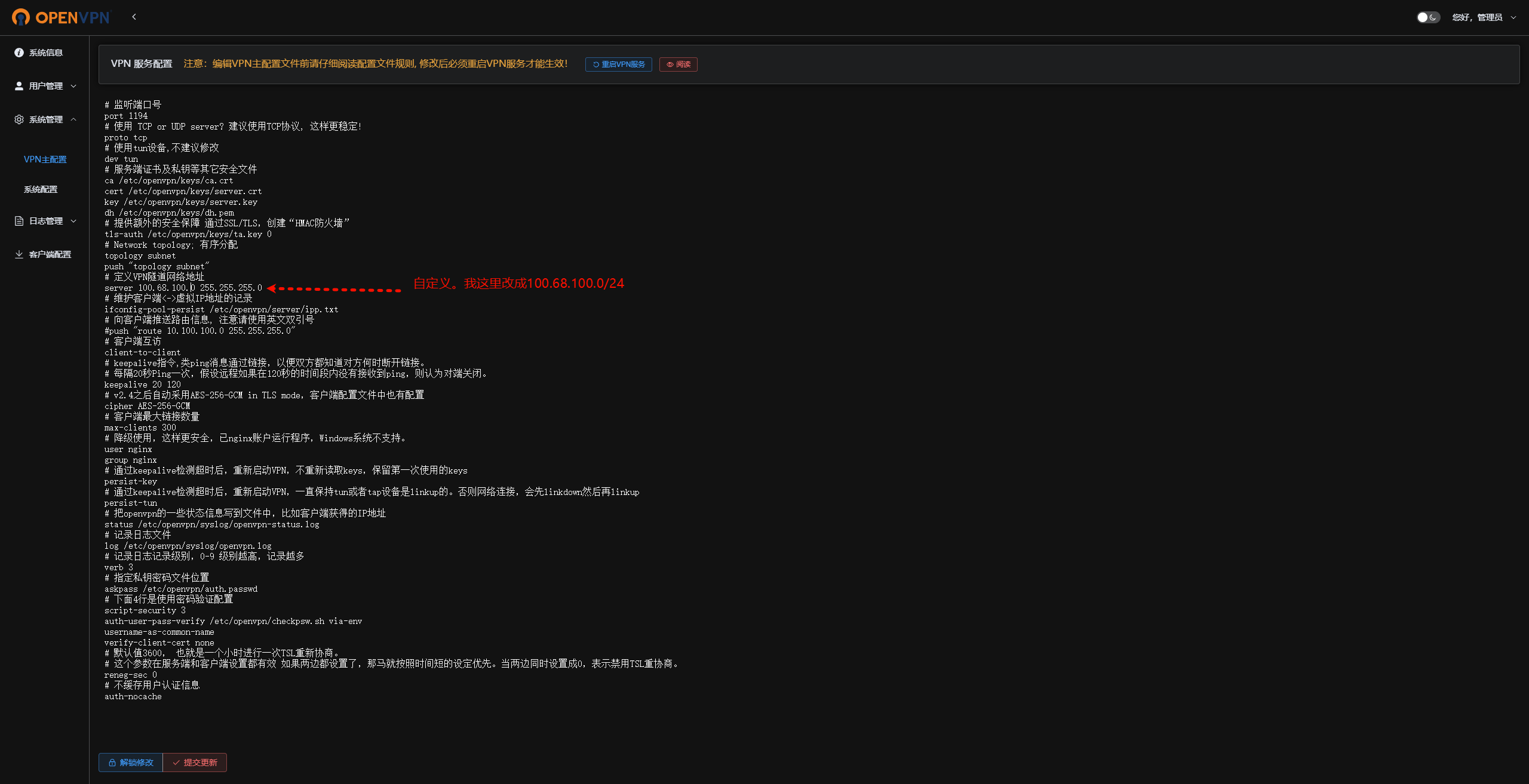
5.4、修改VPN主配置
5.4.1、修改用户虚拟IP段
server 100.68.100.0 255.255.255.0
5.4.2、全局路由走隧道
push "redirect-gateway def1 bypass-dhcp"
5.4.3、指定路由走隧道
push "route 10.0.0.0 255.0.0.0"
push "route 172.16.0.0 255.240.0.0"
push "route 192.168.0.0 255.255.0.0"
5.4.4、指定路由走隧道
push "route 10.0.0.0 255.0.0.0 vpn_gateway"
5.4.5、指定路由走本地
push "route 10.10.10.0 255.0.0.0 net_gateway"
5.4.6、下发DNS
push "dhcp-option DNS 10.225.97.6"
push "dhcp-option DNS 10.225.97.7"
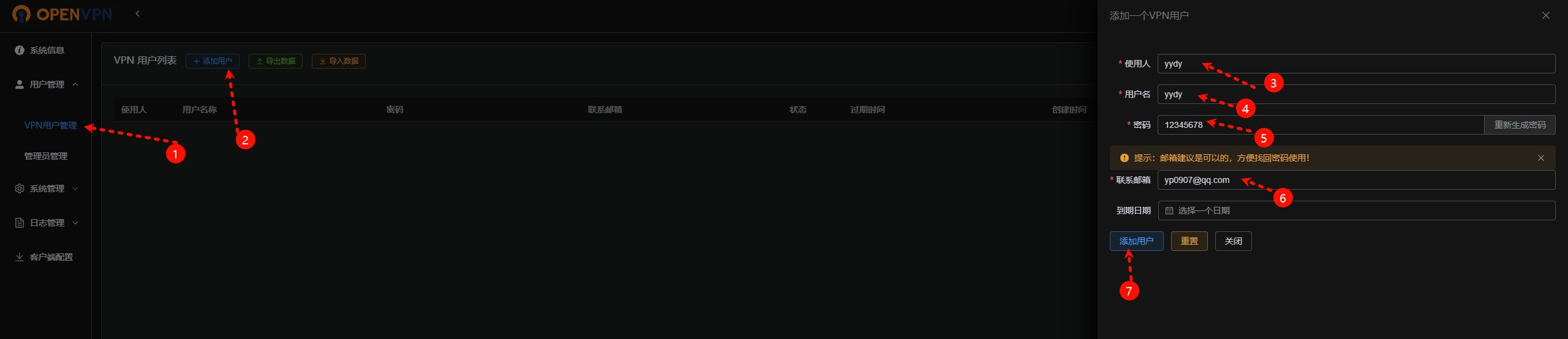
5.5、创建用户
5.6、下载客户端配置文件
5.7、修改客户端配置文件
setenv FRIENDLY_NAME "VyOS OpenVPN"
-
含义:
- 自定义环境变量设置,用于为当前 OpenVPN 客户端或服务实例分配一个名称。
- 它主要用于方便用户区分多个 OpenVPN 服务,或者在 OpenVPN 日志中作为标识来帮助管理员识别不同的配置。
remote yydy.link 29999
-
含义:
- 指定 OpenVPN 客户端要连接的远程服务器的域名或 IP 地址,以及对应的端口号。
yydy.link是远程服务器的域名(可以替换为具体的 IP 地址)。29999是 OpenVPN 服务器监听的端口号(因为我做了端口映射,29999是我的公网端口,内网端口默认还是1194,请注意!)。
-
高级配置: 如果服务器支持多个地址,你可以指定多个
remote选项,OpenVPN 会依次尝试连接:remote main.yydy.link 19999 remote backup.yydy.link 29999
setenv FRIENDLY_NAME "VyOS OpenVPN"
client
dev tun
proto tcp
remote yydy.link 29999
resolv-retry infinite
nobind
key-direction 1
persist-key
persist-tun
remote-cert-tls server
cipher AES-256-GCM
verb 3
auth-nocache
auth-user-pass
reneg-sec 0
<ca>
-----BEGIN CERTIFICATE-----
MIIDSDCCAjCgAwIBAgIUQYD9OcshppQIcT29oiY5TEIy/wkwDQYJKoZIhvcNAQEL
BQAwFTETMBEGA1UEAwwKTGludXhjYyBDQTAeFw0yNDA5MjkwNzQ5NDdaFw0zNDA5
MjcwNzQ5NDdaMBUxEzARBgNVBAMMCkxpbnV4Y2MgQ0EwggEiMA0GCSqGSIb3DQEB
AQUAA4IBDwAwggEKAoIBAQCUrapGQ0Nev3mXHDyBcmiYGNJ2hYrPjIkDi8K3r3Uz
RUrvrkmEIwEVqmeBRVlowt6xMgSrVsLimRlNcEbeAaRYjNhozL3V7BXcu5TvHSiy
NnXJ5Wl5nruztN96TFomcjigFXLj+a4jTSrZ2lZyGibx50qnbpf/fSEV4UmEDScV
vIy+hyh0M80dRqVJUP62sZ7jONBt/159impGV5zkfKKcHhFzPppqQf61pVWgUjx2
e/TAwNu1kZ9D6z2pWPOiEQyTIMnvjZlJINmWHB3QwJiuIBSl+FoZFd1QL5a0PCGX
MgrhyLIQE+AtBsD4ZaSEtDK4l+Gp5FKDoXdLXeMHfxALAgMBAAGjgY8wgYwwDAYD
VR0TBAUwAwEB/zAdBgNVHQ4EFgQUXtQ92s+/pVToDrnG9zRxEe43R8YwUAYDVR0j
BEkwR4AUXtQ92s+/pVToDrnG9zRxEe43R8ahGaQXMBUxEzARBgNVBAMMCkxpbnV4
Y2MgQ0GCFEGA/TnLIaaUCHE9vaImOUxCMv8JMAsGA1UdDwQEAwIBBjANBgkqhkiG
9w0BAQsFAAOCAQEANORlgNwU8ZTNv+blfW5ylrn/YpzpVwCs7viBCUpbzZIvf02W
HBqAoPrQnagc4NoDkCONkEhMmWISLQjdDltRcn76oLWjPWRtj0A4iifkBXEPExwB
Ww43ILMau94aJvcUN8d9cWHOPHdU5XQAXGz5MPKayYP0vT7kxUj0XQVAiTlhnyfr
Ar4DEHVz6IJbgLAEP6MBiGyinzohXas+ISSdZhVZqDUg5x+CMfvP/Iicn8dkk/Ez
bUdcZeFJEVehMX6kj9r0fT4Ex80/dnuiHOlUqw1TjfqQtVD2bIOPXhimt5BROWFP
my3Swr9TFEpLwWdWOtzlDPmLX3ma72psi54ffw==
-----END CERTIFICATE-----
</ca>
<tls-auth>
-----BEGIN OpenVPN Static key V1-----
55df3eca7a8af4d8e49fd633cff1b39d
0c3cefd8053751e068d3cc73df68f297
c7d1fab9bc4640442522668ca6491c80
5b48e5ce571a11da5a145e674938efb3
f34045df059d2b60b26d1b66fec53431
95a097bdc66318985acc914c43ba8e66
8d56ce25392e91a73199400f264b41bf
ec59328db99168ccbe029bce19a2b9a1
6bf1bc86e7357608a05e3754facfbf12
e06ce3c05fe109eb0f7e97032da07938
984d8c2e8fa5f8c169ff4f41d829ed91
346a4954e3d4b78d1cc6076e6fb2d368
3ca87be5ce4e766040343f3d443f9014
227baae0d5c6d197b851027e3f338855
00940a5ff3dddd0dcd9a9a3f4140b0f6
320c3743c2f8686e46224da635f635e4
-----END OpenVPN Static key V1-----
</tls-auth>
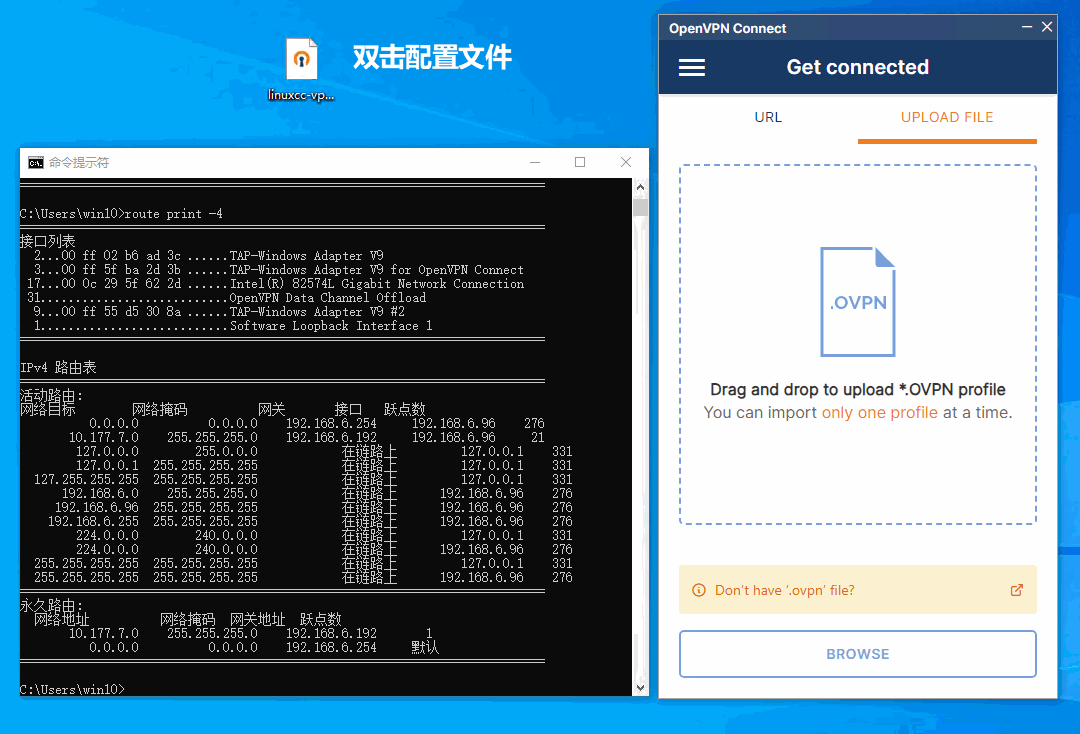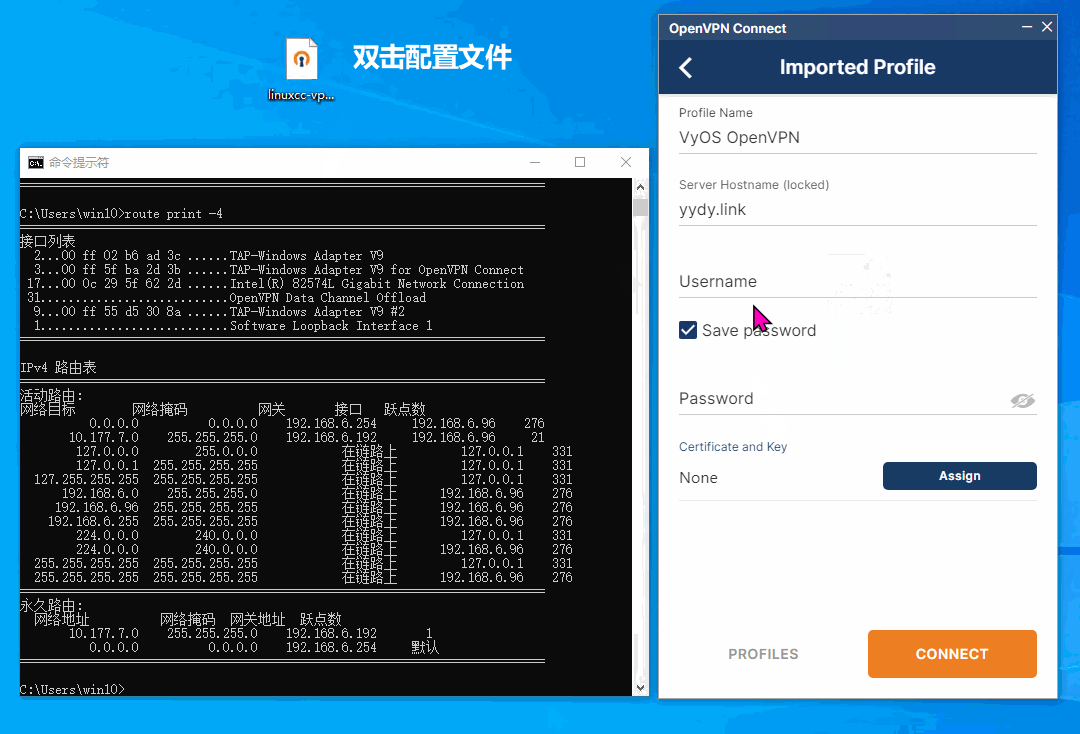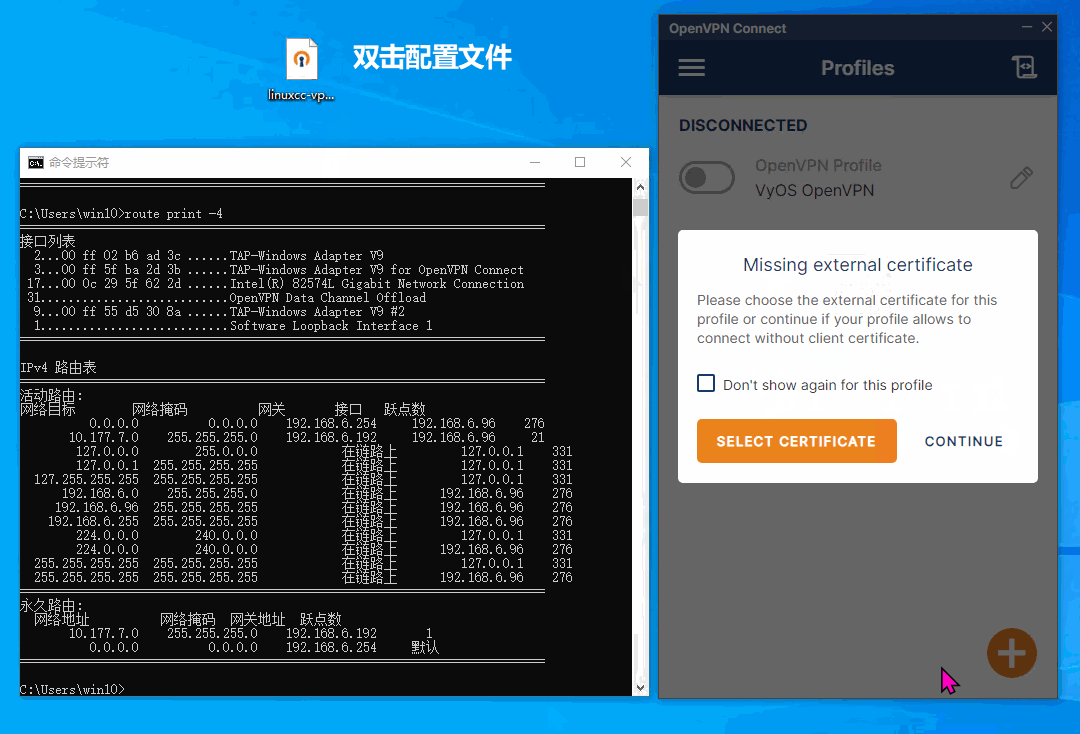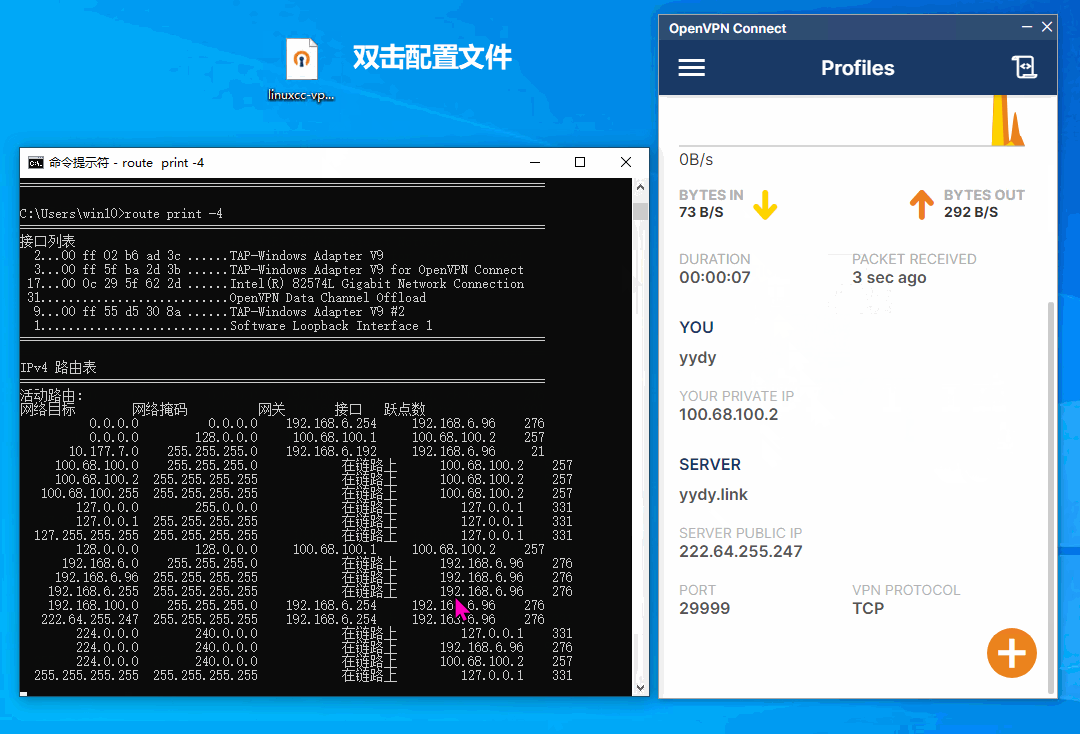
六、连接测试